Port forwarding: What it is and why it’s risky to set it up
Port forwarding can be a powerful tool to unlock new functions on your router, but it can also open serious security vulnerabilities. While NordVPN does not support port forwarding, it’s worth learning what it is and why it’s sometimes used. So what is port forwarding and how can you set it up?
Table of Contents
Table of Contents
What is port forwarding?
Port forwarding is a network configuration technique that enables external devices to access services on a private network, which otherwise wouldn’t be directly accessible from the outside. With port forwarding, you can connect from a local computer to another server, in other words – forward data.
When you set up port forwarding, you essentially tell your router to send some data straight to a specific device on your network, bypassing certain security processes. This can potentially increase your speeds and offer a number of other benefits.
However, port forwarding has its risks. We do not not encourage you to use port forwarding, and it’s important to remember that NordVPN is not compatible with port forwarding. That said, let’s explore the technical side of port-forwarding in more depth.
How does port forwarding work?
To understand port forwarding, you first need to understand what your router does. Think of your router as a mix between a security guard and a mail sorter. Your NAT firewall, which resides on your router, sends incoming connections to the devices that requested them, by extension also blocking unwanted incoming data. It does this automatically, but if you want your home devices to connect to a remote device, you need to set up port forwarding.
Your router has over 60,000 ports. About the first 1,000 are ordinarily dedicated to standard specific functions. The remaining can be assigned to any device or program you want. You can do so by opening a port on your router and assigning it to a specific device. Now, when a device sends a connection request to your router, it will automatically create a direct connection. To do so, you will have to know your port number. Here’s how to find your port number.
Again, it’s worth noting that port forwarding will not work with NordVPN, and we don’t encourage people to use this process.
What is the purpose of port forwarding?
Port forwarding is useful whenever you need to make a direct connection between a device in your home network and a remote device. For example:
- Watch a security camera or baby monitor when you’re away from home.
- Connect to your home server remotely.
- Use remote desktop software to access your home computer.
- Allow other users to connect to your public web server.
- Connect to an IoT device on your home network.
- Form a direct connection to a gaming server.
- Maintain uninterrupted and direct access to a VoIP call server.
There are many other legitimate uses for port forwarding, but many of them are advanced and beyond the scope of this introductory article.
PRO TIP: Please note that NordVPN does not support port forwarding. But if you use NordVPN’s Meshnet feature, you don’t need to configure firewall rules or set up port forwarding to establish a connection with a remote device.
Types of port forwarding
There are various port forwarding types that serve the different needs of network users and applications. Here are the main types.
Static port forwarding (also known as port mapping)
Static port forwarding involves adjusting router settings manually to establish rules that direct internet traffic to a specific device within a local network, using a designated port number. This process is also referred to as port mapping.
You could use static port forwarding in your router settings to create a direct pathway for accessing your home surveillance system from anywhere over the internet to keep an eye on your home security while traveling.
Local port forwarding
Local port forwarding allows you to forward traffic from your local machine to another server via an intermediary, usually through an SSH tunnel.
Imagine you are working from a coffee shop and need to access your company’s internal database securely. By setting up local port forwarding through an SSH tunnel, you can create a secure connection from your laptop to the database as if you were accessing it from within your company’s network.
Remote port forwarding
Remote port forwarding is the process of forwarding a port from the remote server back to your local computer or another destination. Essentially, remote port forwarding allows external access to services hosted on your local machine through a secure channel, like an SSH tunnel.
Let’s say you’re developing an app on your local computer and want to show it to your client without deploying it to a public server. By using remote port forwarding, you can allow external access to your application running locally.
Dynamic port forwarding
Dynamic port forwarding allows you to create a flexible, secure tunnel through which traffic from various ports can be sent to multiple destinations, based on real-time requests, typically using SOCKS proxy protocols.
You could use dynamic port forwarding when you need to access your email or a work database securely while traveling and using public Wi-Fi. This type of port forwarding can act like a secure tunnel for your internet traffic, routing it through your home or office network.
UPnP port forwarding (Universal Plug and Play)
You might have previously used port forwarding without actually manually configuring the ports or even being aware of it. How? Your device used Universal Plug and Play (UPnP), which allows apps on your device to open ports on your router when needed and to close them when they’re done. UPnP facilitates seamless communication and data exchange between devices within a private network and external devices or services.
NAT port forwarding (network address translation)
NAT port forwarding is a network configuration process where a network address translator (NAT) modifies the destination address and port of the incoming traffic to route it to the appropriate internal IP address and port.
For example, if you want to play games with your friends online, you can use NAT port forwarding on your router to allow your friends to connect to your gaming server at home.
How to set up port forwarding
The specific instructions for port forwarding can be different for each router or brand, so here’s a general overview of what the process might look like:
- Log into your router. You can do so by entering your router’s IP (or in other words, default gateway) into your search engine’s address bar. Then enter your admin username and password and press “Login.”
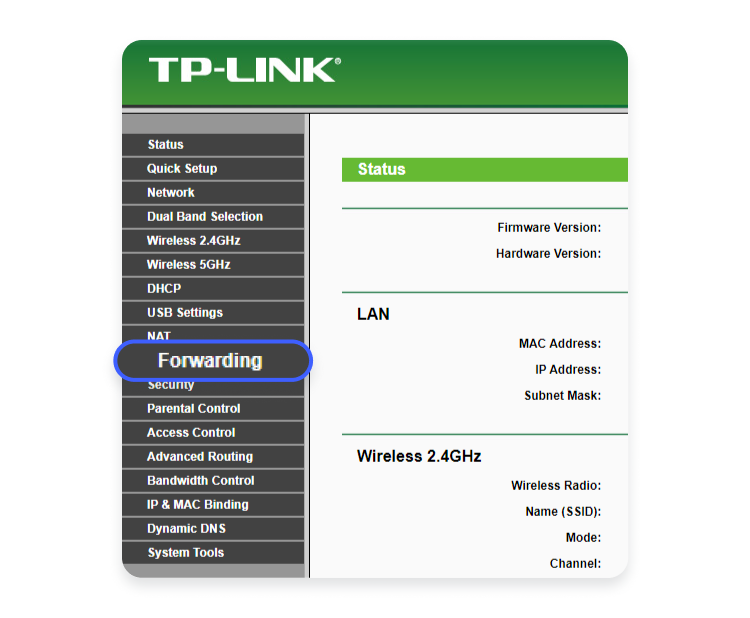
- Open the port forwarding settings panel. Although each router’s interface is different, the section you need will typically be labeled “Forwarding,” “Port forwarding,” “Firewall,” or something similar. Find the relevant menu item and click on it.

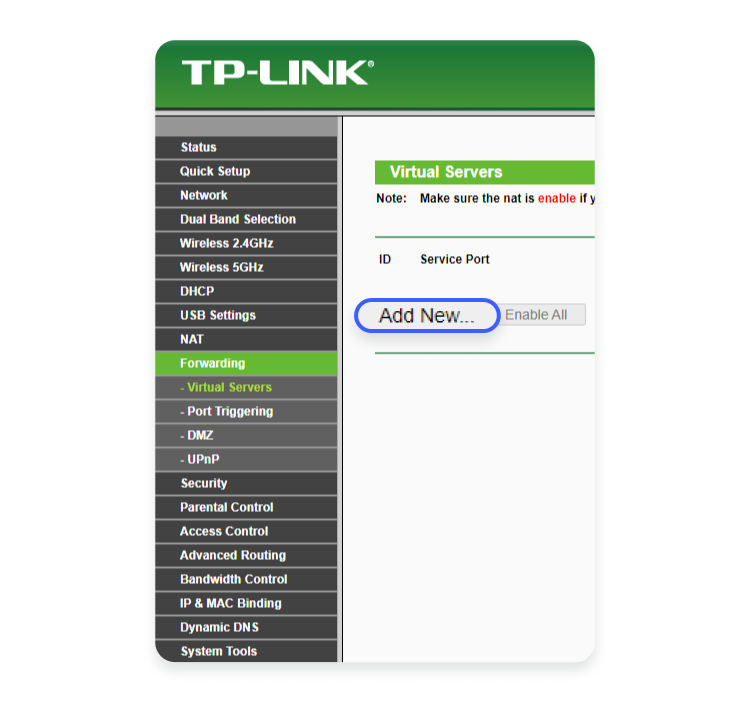
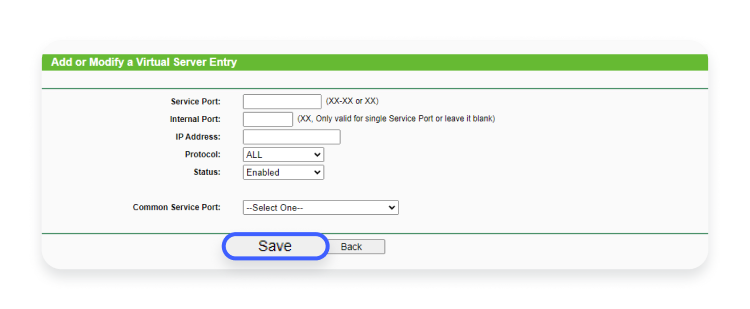
- If you’re using a TP-Link router, select the “Virtual servers” menu item in the drop-down menu.

- Click “Add new” or “Add rule” to create a custom port forwarding entry.

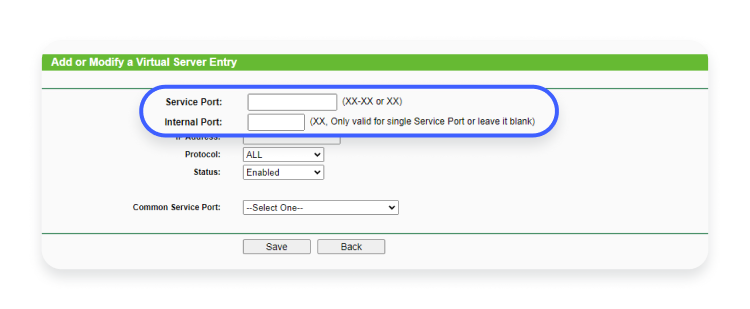
- Choose one configuration and enter internal and external port numbers. The external port is the number that devices on the internet use to reach your network, while the internal port is the number on which a device inside your local network awaits incoming connections. In most cases, the external and internal ports don’t actually have to match each other, as long as the external and internal devices know which ones to use.It’s important to ensure that there are no conflicts with other services using the same ports.

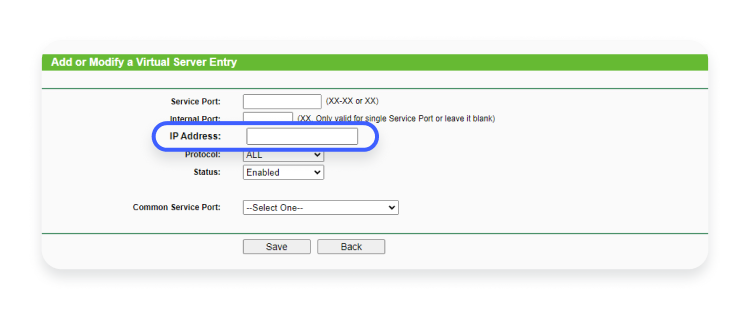
- Once the ports are set, enter the local IP address of the device you want to connect to (the local address will be different from your router’s IP address).

- Click the “Save” button to save your settings.

Now the router can redirect any request sent to that specific port straight to your device without revealing its private IP address. But what does that request look like?
Say your device’s IP address is 192.168.1.100. If the port you set to connect to your home security camera is 554, then a request to your device to connect directly to the camera via port forwarding would be sent to this address: 192.168.1.100:554. It’s just like dialing a phone number with an extension.
You can also set up port forwarding to enhance your online gaming experience. Port forwarding your PS will boost your connection speed and give you a more enjoyable gaming experience. Same goes for port forwarding your Xbox One – it will improve speed and reduce latency.
How can you test port forwarding?
Once you’ve configured port forwarding, you should check if the ports are open and functioning properly. The easiest way to test port forwarding is to use an online port checker tool like canyouseeme.org. There are multiple online websites that provide this service for free.
Here is what you have to do:
- Go to the online port checker website.
- Enter the port number you’re forwarded in the designated field.
- Click on the “Check port” or a similar button.
You might get these results when using a port forward checker:
- “Port is open” means you’ve correctly configured your port forwarding settings and the service associated with that port is accessible from the internet.
- “Port is closed” signifies that your port forwarding settings might be incorrect. Check your router configuration and make adjustments.
- “Port is filtered or blocked” means that something is preventing the traffic on that port from flowing freely to its intended destination. It could be that your internet service provider (ISP) is restricting traffic on that port. Or it might be that some firewall rules or other security measures on your networks are blocking or filtering certain types of traffic.
Is port forwarding safe?
Yes, port forwarding is safe if configured correctly. However, incorrect configuration can lead to increased exposure and vulnerabilities in your network.
Imagine that your router’s ports are doors, and most of them are locked. The information from the internet can still get in – it just has to be checked and allowed in by the router. But when one of those doors is unlocked, anyone who tries that door can open it and walk right in.
In one sense, it’s not as bad as it sounds – that opened port (or unlocked door) only leads to whichever device it was pointed at. But as we’ll explain, there are many ways in which port forwarding can leave you vulnerable to online threats.
Does port forwarding work with a VPN?
VPN port forwarding allows incoming data to get around your NAT firewall, speeding up your internet connection. There are several reasons to use VPN port forwarding. It can increase your download speed, help you to access your computer when you’re away, and form a direct connection with a gaming server.
Port forwarding and triggering could work with a VPN protocol in general, but not with NordVPN. Our apps block almost all port communication from within your device except for the ones most commonly used by popular applications. This was a tough decision that may inconvenience some users, but there’s an explanation for it.
Browsing the internet with open ports exposes you to a number of security risks. Blocking access to all ports except those that are essential for VPN functionality is part of how NordVPN keeps you secure. Otherwise, we wouldn’t be able to ensure your safety online.
If you aren’t yet covered by a VPN, download a VPN app for free and find the subscription that works best for you. Once you launch the app, you’ll be protected by some of the best encryption in the industry.
Port forwarding vs. port triggering
Port triggering is a configuration feature on a NAT-enabled router that manages the flow of communication between internal and external host machines in an IP network, opening inbound ports in response to specific outbound traffic.
Port triggering is a little different from port forwarding. Some of these differences help shore up some of port forwarding’s security vulnerabilities, but they also limit the cases where port triggering can be useful.
First, when you set up port triggering, the port you choose remains closed. It will only open in the event of being triggered by outbound communication.
When the outbound communication that triggered the port opening ends, the port will close after a specified period of time. This makes the connection more secure because it puts the local device in control of opening the connection. However, it also means these connections are difficult or almost impossible to initiate from the outside.
Secondly, port triggering doesn’t require you to configure a specific device IP address when creating the trigger. This means that any device on your network can initiate the connection, though only one can use it at a time. In port forwarding, you have to define the specific device using the connection. Depending on your router and your devices, this can make port triggering either a more or less secure choice than forwarding.