What is DNS hijacking?
DNS hijacking is a serious online threat that often goes unnoticed. Even worse, it’s conducted by exploiting a fundamental layer of the internet that is essential for its functionality and convenience.
Table of Contents
Table of Contents
How DNS hijacking works
DNS, short for Domain Name System, makes your internet browsing effortless. DNS functions as an interpreter between humans, who talk words, and computers, who talk numbers.
How DNS works
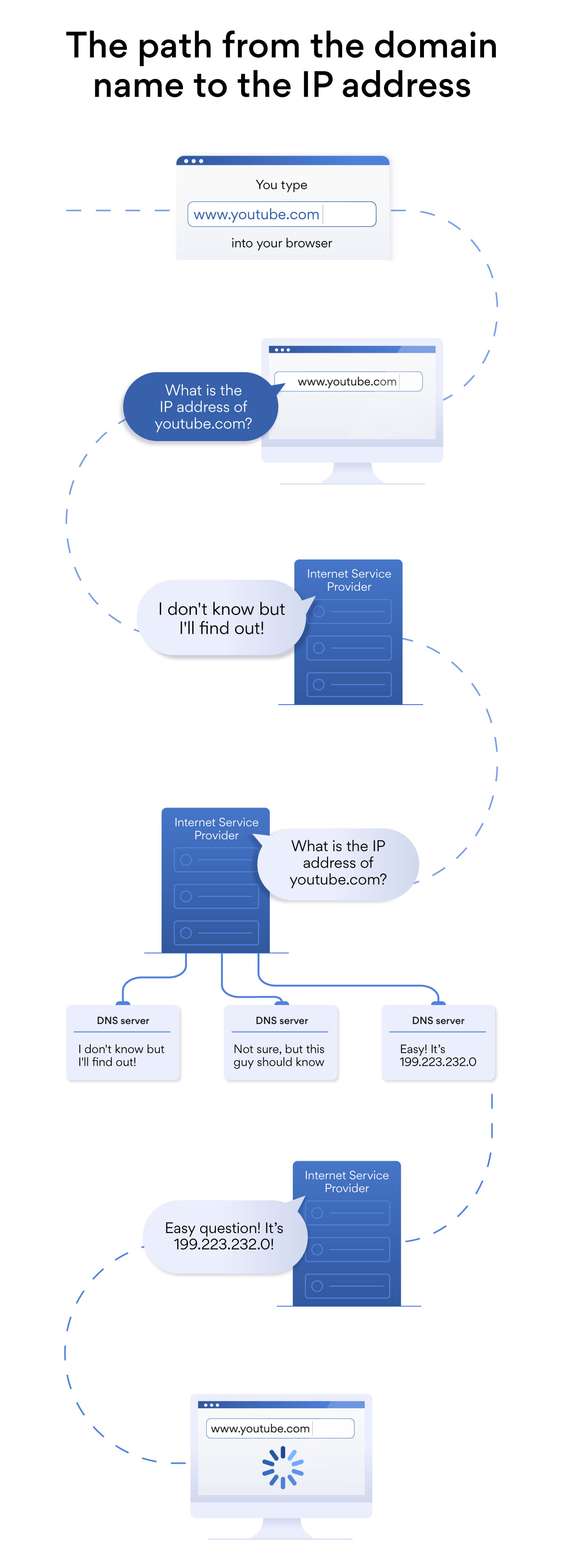
When you type in a website domain (youtube.com), your device needs the IP (199.223.232.0) to actually go there. It gets it by sending a query to a DNS server – a special kind of server that has a database of IP addresses and their associated hostnames.
Your device: “What is the IP address of youtube.com?”
DNS server: “It’s 199.223.232.0.”
Your device accesses youtube.com.
You watch your favorite vlog without ever thinking of the inner-workings of the internet.
If only it were that simple. Your query “What is the IP address of youtube.com?” actually goes through multiple DNS servers before coming back to you with an answer.
Imagine that the internet is a colossal virtual highway system. To visit a website, you have to get in a car and drive to your destination without any map or GPS.
You would get lost at the first crossroads you hit – but that’s where DNS saves the day. Like a traffic officer, the DNS server directs you towards the next crossroads, where another DNS server directs you to the next crossroads until you reach your final destination.
Eventually, you will be led to an authoritative nameserver that provides the IP address you’re looking for. Voila, YouTube videos on your screen.
If you ever wonder “what is my DNS,” you can check your device’s network settings or use online tools to see which DNS server is resolving domain names for you.
What makes DNS vulnerable?
- DNS was created in 1985. The net was in its infancy, its participants were few, and everyone was trusted by everyone else. As the internet grew, DNS grew with it. Patched up, updated and scaled up, it has survived to this day. Unfortunately, attackers have become much more sophisticated since the DNS system was created.
- The system is based on trust, but not every DNS is trustworthy. Compromised or malicious DNS servers open the system up for exploitation.
How does DNS hijacking work
As you can see, DNS is highly decentralized. No single DNS server holds all the IP addresses and their corresponding domains. Your query will travel along a chain of DNS servers before you get your result.
DNS hijacking is the practice of redirecting DNS queries. You send out a query – What is the IP of youtube.com? – but a third party steers the query the wrong way. As a result, you get a false IP address, and the wrong page loads on your screen.
Say you’re trying to access your online bank. Your DNS is hijacked and a different website is loaded that looks exactly like your bank’s homepage and you enter your login details. This is a known phishing scam when hackers create fake copies of a website to extract their victims’ usernames and passwords. The next thing you know, your bank account has been emptied.
In other cases, DNS hijacking can be more annoying than harmless. When you type the URL of a website that does not exist, you should get an error message. However, some internet service providers redirect you to their website to show you ads instead.
The bad news is, anyone can be susceptible to DNS hijacking.
How does your DNS get hijacked?
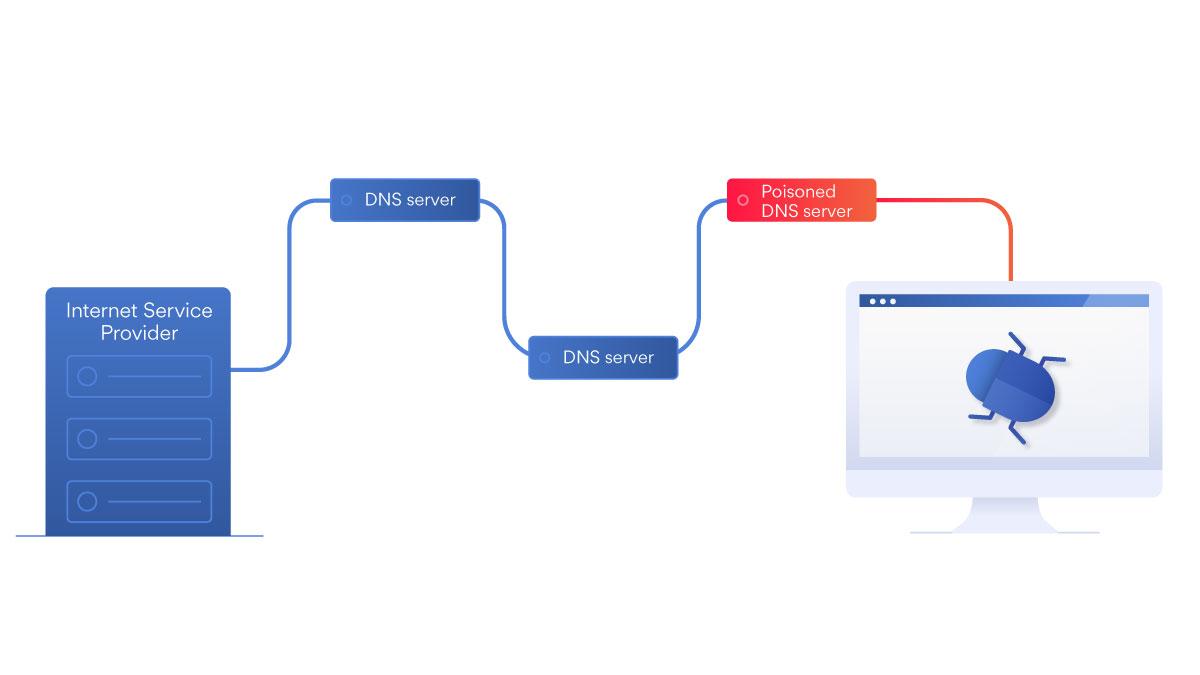
A DNS hack could happen at any link in the chain of DNS queries. Here’s how:
Malware
Your computer or router can be infected with malware that rewrites the configuration of DNS settings. As a result, your device queries a rogue DNS server that serves you fake IP addresses.
The most famous malware of this kind was called DNSChanger, which wreaked havoc on the net until it was put down in 2012. It infected computers and changed their DNS configurations, pointing them to rogue servers operated by hackers. These servers replaced advertising on websites with ads sold by hackers, making them $14 million in profit (to find out more about other types of malware, click here).
In total, over four million computers were infected. Their owners had no idea they were seeing ads placed by hackers who had corrupted their systems.
This scenario could have gone much worse. A more malicious malware could redirect you through hacker-controlled open web proxies and get access to all your traffic (and any sensitive data you send). You could also be directed to a dummy website that extracts your passwords and usernames through fake login procedures.
The worst part of a malware attack is that you have no idea that your system is compromised until the damage is done.
Compromised DNS server
In a DNS server hack, your query is redirected in the wrong destination by a DNS server under a hacker’s control. This attack is even more cunning because once the query leaves your device, you have no control whatsoever over the direction your traffic takes.
Essentially, they violate the trust your system places in DNS servers. Hacking a DNS server will usually be relatively difficult, but it’s far from impossible.
Internet service provider interference
Some internet service providers use DNS hijacking on their own users to display ads or collect statistics. They do this by hijacking the NXDOMAIN response.
NXDOMAIN is the response you get if you type in a domain that does not exist (meaning it doesn’t have a corresponding IP address). For example, if you entered “ssdsrfadsfdgfaaf.com” into your browser, you would get the NXDOMAIN response: “The website cannot be found” or a similar error message (unless someone were to buy that domain for some reason).
When an internet service provider hijacks the NXDOMAIN response, they replace the error message with a fake website set up by the internet service provider to show you ads or collect your data.
DNS hijacking cases
Here’s a quick run-through of the most famous DNS hijacking cases:
WikiLeaks
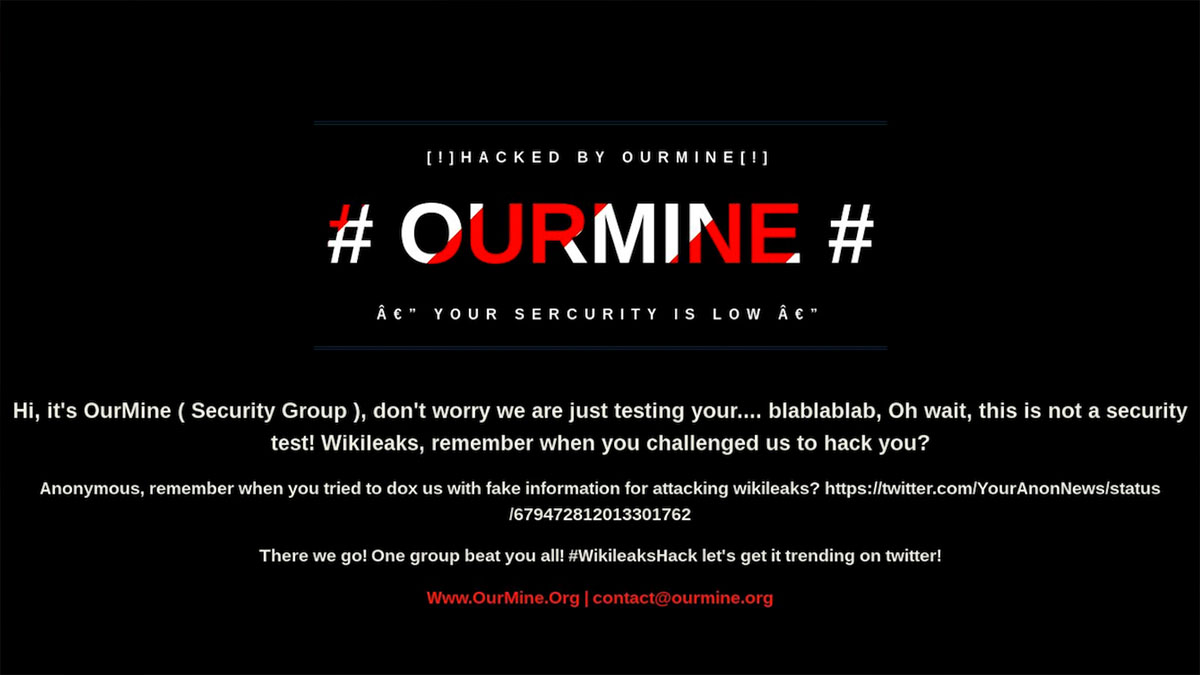
Anyone who tried to visit wikileaks.org on August 30, 2017 saw an ominous message claiming that the website, famous for storing and publishing classified and secret information, had been hacked.
A hacker group called OurMine took credit. “Wikileaks, remember when you challenged us to hack you?” they taunted the website on its own homepage. From a visitor’s standpoint, it appeared that Wikileaks’ servers have been compromised and that the site was under total hacker control.
That was not the case.
Wikileaks was up and running and its servers were secure. If you knew the IP address, you could reach and browse the website without any hassle. In reality, the hackers had hijacked one of the DNS servers that directed visitors to wikileaks.org and sent users fake values.
As is common in these cases, the details of how this was done are not known. Hackers may have used malware or knew someone on the inside with administrative access or used phishing to get usernames and passwords.
Brazilian banks
For five long hours on October 22, 2016, hackers had total control over the domain of a major Brazilian bank with hundreds of branches, over 5 million customers, and $27 billion in assets.
The attackers launched the attack by compromising the DNS server of Registro.br, which is the registrar for the top-level domain .br and manages the DNS for the Brazilian bank (its name was not disclosed by the researchers who discovered the hack).
The hackers redirected users to their own servers that looked exactly like the bank’s homepage, but were, in fact, fakes meant to extract user login credentials. Users, directed to the fake sites, handed their usernames and passwords to the hackers and were infected with malware.
No one knows how many people were defrauded by the hackers and had their personal data compromised. This case was reported by the security firm Kaspersky, which did not disclose the name of the bank, nor did the bank itself come forward. This is the usual practice in cases like these. The idea was to protect the victims while informing cybersecurity experts about potential vulnerabilities.
New York Times
In 2013, the Syrian Electronic Army hacker group compromised the website of the Melbourne IT domain registrar and changed the records of Melbourne IT customers. One such customer was The New York Times, whose website was replaced with the logo of the Syrian Electronic Army.
The Syrian Electronic Army used the same vulnerability to disrupt Twitter.co.uk and HuffingtonPost.co.uk.
How to prevent DNS hijacking
- Use reliable antivirus software and update your system whenever security patches come out. Malware that modifies DNS settings is the most common form of DNS hijacking. For malware prevention, also use NordVPN’s own Threat Protection Pro tool. It neutralizes cyber threats before they can do any real damage to your device. It helps you identify malware-ridden files, stops you from landing on malicious websites, and blocks trackers and intrusive ads on the spot.
- Avoid suspicious links. Cybersecurity 101 – do not click on links from sources (people, websites) you are not familiar with. Even if you trust the source, check the URL carefully.
- Use a VPN, which encrypts your traffic and prevents hackers from intercepting and snooping on your sensitive information. A VPN is especially useful if you frequently use public Wi-Fi, which is often unsafe due to poor router configuration and weak passwords. Moreover, NordVPN also has the private DNS feature. By encrypting all of your online traffic, NordVPN shields your DNS requests from third parties. This means no one can spy on you or secretly redirect you to a malicious site.
- Change your router password. It’s very easy to crack the default factory login, so a hacker is just a step away from changing your DNS settings. We have plenty of tips on creating strong passwords here.
- Be alert, especially if a website you are familiar with acts like a stranger (gives you weird pop-ups, screens, shows landing pages you’ve never seen before). Alertness is key since there is no foolproof protection against the types of hijacking attacks that targeted The New York Times or WikiLeaks. In those cases, authoritative DNS servers, which hold actual records, were poisoned.
- Change to a secure DNS server. Your DNS can be changed to a more secure one. If the DNS servers operated by your internet service provider are underperforming, you can choose a third-party server to increase your privacy and improve connection speed. But always do your research to find out which public DNS servers are safe to use.
Want to read more like this?
Get the latest news and tips from NordVPN

