Threat Protection: NordVPN’s solution against phishing
With so much online content at your fingertips, it’s easy to click on a random link or a bright ad without thinking twice. But that’s how you might end up on a phishing website and put your privacy at risk. That’s why NordVPN created Threat Protection Pro – a solution that inspects links and websites when you’re too busy or distracted to do it yourself. Take a look at how Threat Protection Pro helps you avoid phishing attacks and browse safely.
Table of Contents
Table of Contents
What is phishing?
Phishing is a type of cyberattack where criminals pretend to be a reliable person or organization to trick you into sharing sensitive information. They do so via emails, text messages, and phone calls as well as fake websites.
For example, you might receive an email that looks like it came from your bank, prompting you to click on a link. The layout, images, and even wording might resemble legitimate emails you’ve received before. Once you click on the link, it directs you to a phishing website where you’re asked to provide your login credentials for your online account or some other personal data.
There are many types of phishing, but all of them share the same goal – to lure unsuspecting users into sharing information that cybercriminals will later use for financial or identity theft, or simply leak it on the dark web.
The evolution of phishing
The example in the last section describes a very basic and common phishing type – email phishing. Unfortunately, phishing campaigns are becoming more frequent and sophisticated by the day.
The phishing attempts of old were rather simple and usually consisted of generic greetings and poorly constructed messages, so they were easy to identify. Present-day phishing attacks involve targeted social engineering tactics to make the communication more believable. If your “bank manager” urges you to confirm your personal information for security purposes, wouldn’t you click on the link in the email and do what you’re asked? If you did, however, you could end up on a phishing website.
Phishing websites
Cybercriminals are now widely using phishing websites to get hold of personal user information. A phishing website is a fake website that mimics a legitimate one. These are digital traps set by cybercriminals to steal passwords, credit card details, and Social Security numbers.
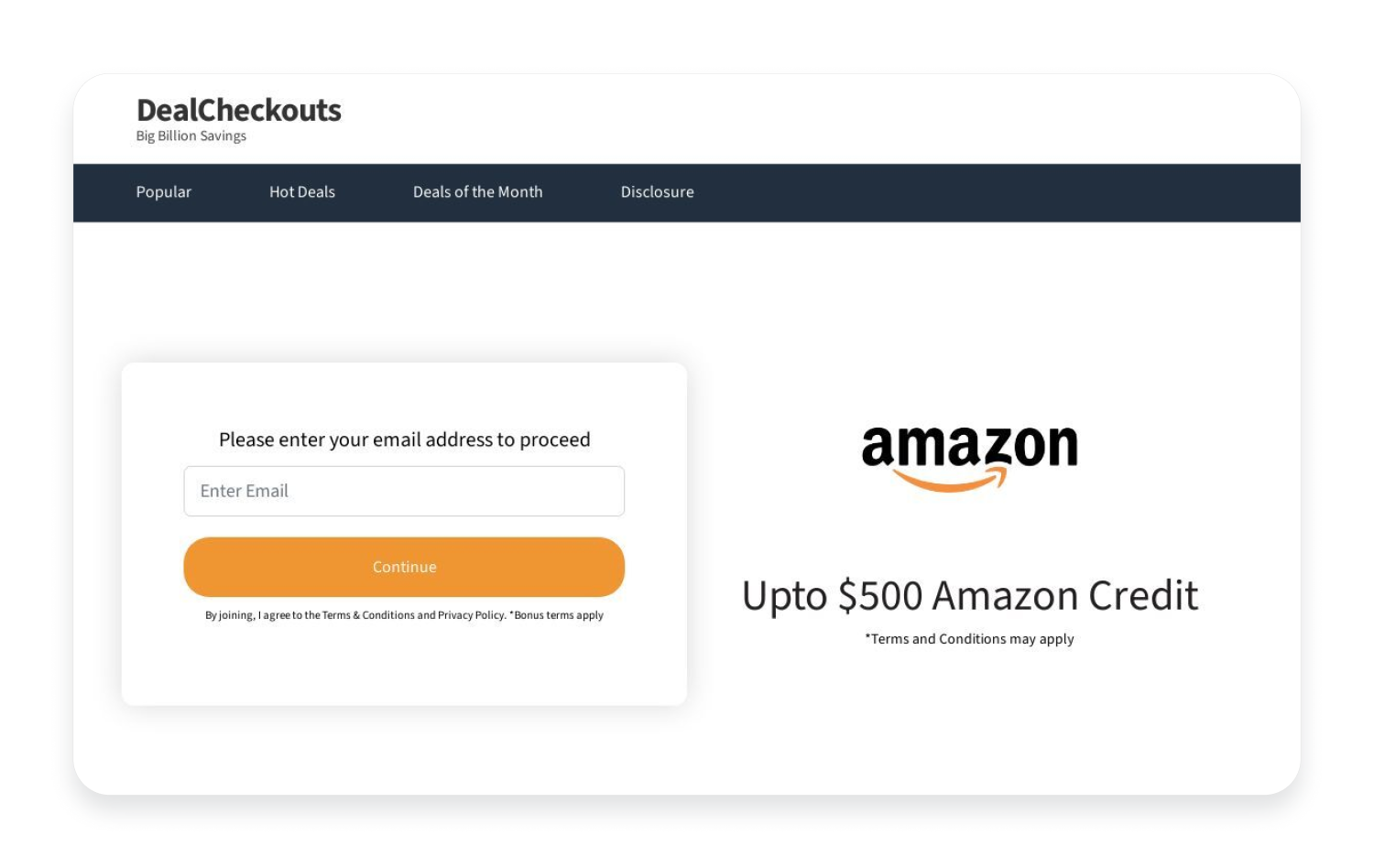
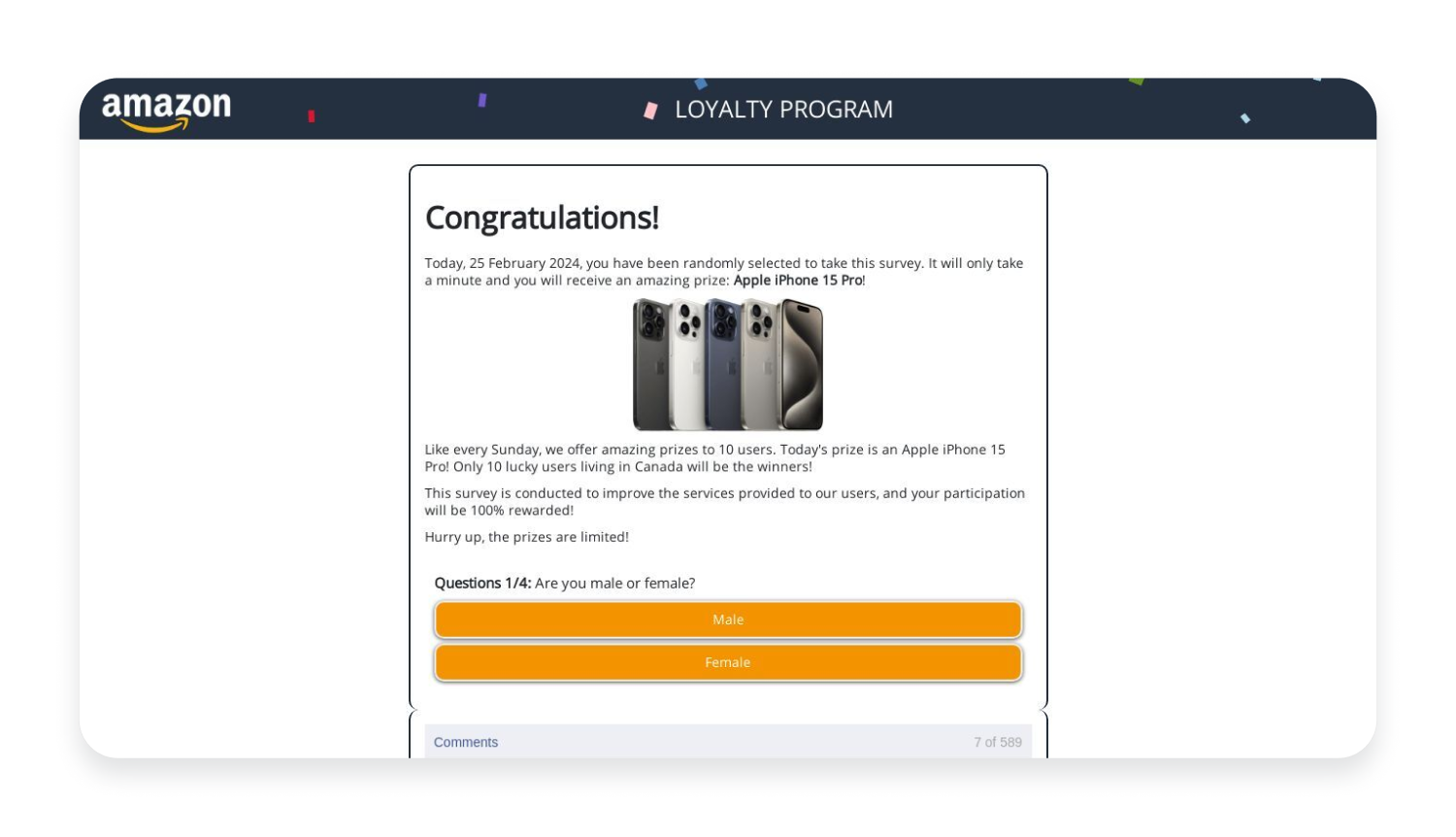
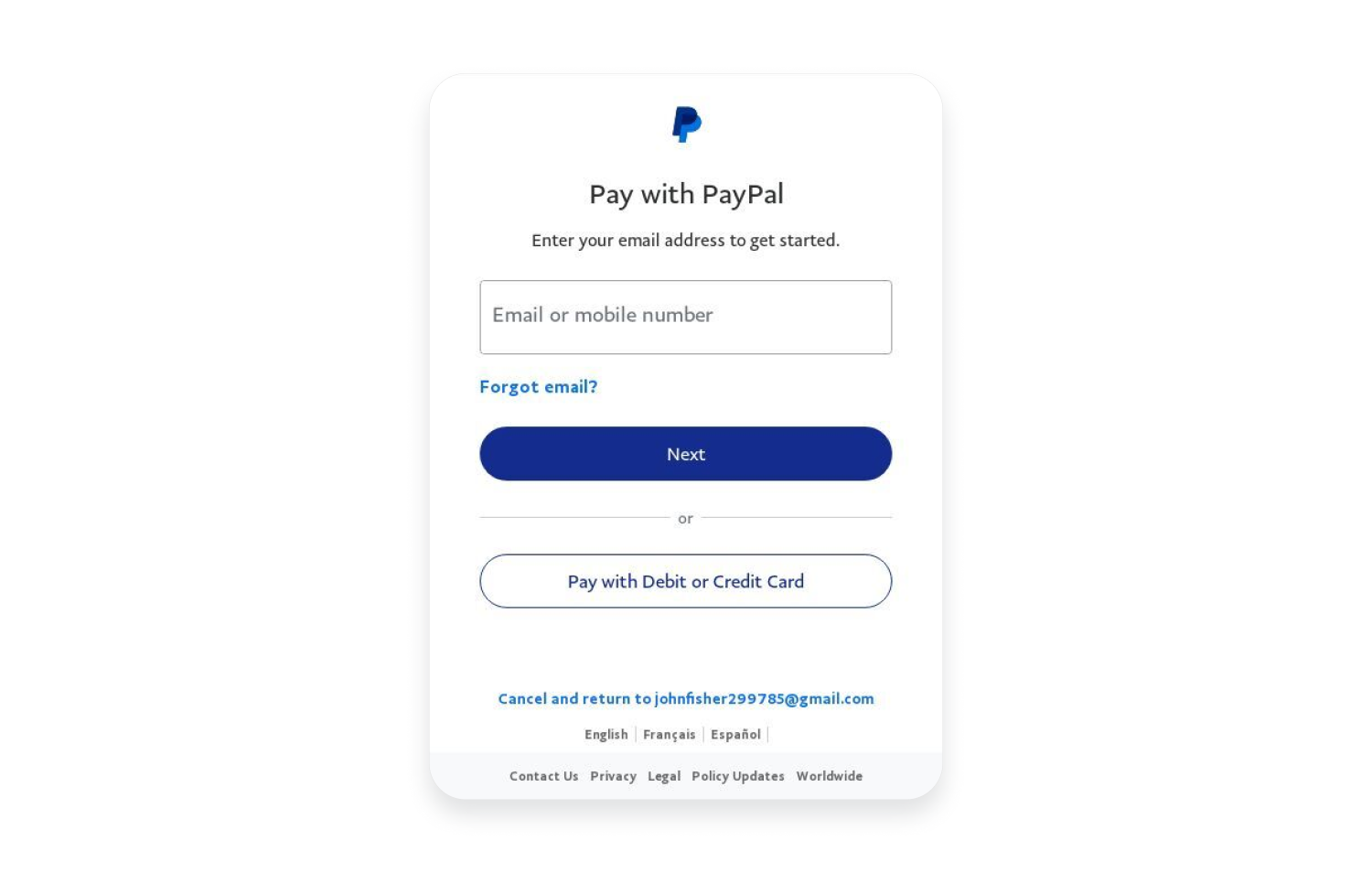
Here are a few examples of phishing websites that resemble Amazon’s, PayPal’s, and Microsoft Outlook’s web pages.
Amazon phishing examples:
PayPal phishing example:
Outlook phishing example:

As you can see from the screenshots, some fake web pages look incredibly similar to legitimate ones, if not completely identical. Some phishing websites even redirect you to the real website after collecting your credentials to further fool you.
Zero-day phishing attacks
Another development in the cyberattack landscape is zero-day phishing attacks. These are sophisticated attacks that take advantage of zero-day vulnerabilities in software or systems. Zero-day phishing attacks are effective because they exploit flaws that the vendor is unaware of and hasn’t yet fixed.
It’s very difficult to tell apart a well-fabricated website from a legitimate one, especially if it’s a zero-day phishing attempt. Here is where NordVPN’s Threat Protection Pro solution comes in – it helps you avoid phishing attacks on websites, including zero-day phishing. Now we’ll walk you through what it does and how it protects your privacy.
Threat Protection Pro: A solution based on machine-learning
Our ML-based solution recognizes fake websites that impersonate legitimate ones and warns you about them. If you ever stumble upon a phishing website, Threat Protection Pro will block the page and inform you about the threat with an on-screen message:
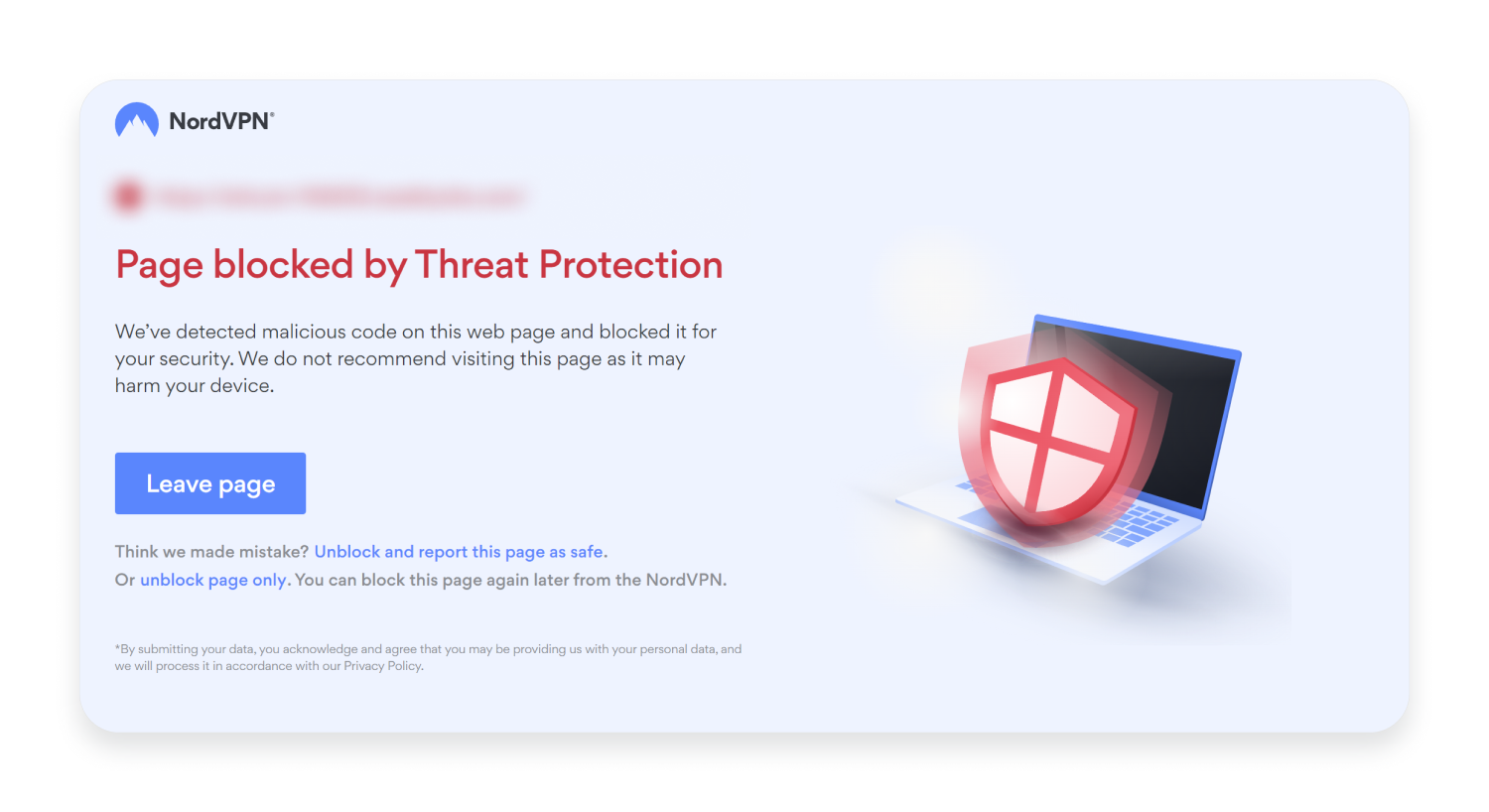
Simply leave the page to stay safe. But let’s look into how Threat Protection Pro detects phishing websites.
How Threat Protection Pro works against phishing
Our Threat Protection Pro tool determines if a website is a phishing website or not. Here are the four lines of defense that our data science and malware teams work on to make Threat Protection Pro the powerful anti-phishing tool that it is:
- We collect datasets of URLs that could potentially be phishing URLs using our own collection tools and external providers.
- Our URL reputation service aggregates verdicts from different reputation sources to assess the credibility and security of web addresses.
- We analyze URL information, including certificates and domain age.
- We use ensemble machine learning models that rely on the HTML content, the visual representation, and the metadata of the URL to determine if the content of the URL belongs to one of the brands in our Threat Protection Pro database.
This combination of methods ensures that we block many phishing attempts, even when other vendors classify websites as clean. Running ML on all URLs is not always the most efficient or cost-effective approach. That’s why we’re using a layered solution – it’s more effective and allows us to offer this service for a reasonable price.
Machine-learning for phishing detection
Our approach is based on a sophisticated machine learning algorithm that we trained using a large set of data to characterize different representations of each brand in our ever-expanding database. This data included both malicious and benign websites. As a result of this thorough training, Threat Protection Pro distinguishes between phishing and legitimate websites with precision.
The adaptability of the system is another significant trait. Through the use of machine learning, the system is able to adapt its detection skills by continually learning from both new phishing occurrences and legitimate websites that are continuously changing. This ongoing learning ensures that Threat Protection Pro keeps up with ever-evolving phishing tactics.
Phishing attack statistics
Our deep learning model works on the visual aspect of the web page – the image you see on your screen when you visit a web page. Our model determines if a legitimate website is represented in the image or a fake one.
According to the Threat Protection Pro phishing attack statistics for February 2024, we checked 600,000 newly created websites, 3,000 of which were classified as zero-day phishing attacks. Our solution protected users from every single one of these phishing attempts.
Popular brands and services are frequently abused by phishing attacks. Take a look at the zero-day phishing statistics concerning some well-known brands. Here is how many phishing websites pretending to be popular brands Threat Protection Pro detected in February alone:
These zero-day phishing attempts are just a fraction of all phishing attempts that Threat Protection Pro detects on a monthly basis, and only a small sample of brands from our database. Our data science and malware teams are working on adding more brands to our phishing detection service database to protect our users from as many phishing scams as possible.
Recognizing phishing attempts
Given the level of sophistication and quantity of phishing attacks, it’s crucial you recognize them and not fall for the trap. Here are some common phishing signs to look out for:
- Threats and urgency. Phishing emails and text messages frequently raise panic and urge you to take quick action, for example, update your information to avoid account closure.
- Unsolicited requests for personal information. Reputable companies almost never send emails asking for private information. It’s better if you delete emails asking for credit card numbers, passwords, or other private information.
- Spelling and grammar errors. Reliable organizations usually make sure that their email correspondence is error free. Treat spelling and grammatical errors as red flags.
- Missing URLs. Hover your cursor over the links in the email but do not click on them. If the URL appears strange or doesn’t fit the email’s context – it’s probably phishing.
- Requests to verify account information. Treat emails asking you to verify your account or password with caution, especially if the email urges you to do so via a link.
- Offers that seem too good to be true. Scammers may use emails or web pages that offer astonishing discounts, lottery winnings, or surprising rewards in an effort to get your personal information.
How to protect yourself from phishing
Recognizing a phishing website upon first glance might be impossible, especially if you’re not looking for red flags. Even if you look out for the signs of phishing, some scams are so elaborate that you’ll still need a security tool to spot them.
By subscribing to NordVPN’s Ultra, Complete, or Plus plans and downloading the NordVPN app, you get our Threat Protection Pro anti-phishing solution as part of the package. It will block malicious websites, stop web trackers, and even remove annoying ads. Keep Threat Protection Pro on at all times and browse with confidence!
