What is port 443? Technical guide about HTTPS port 443
If you’ve ever looked closely at the browser’s address bar when visiting a website, you’ve probably noticed either the HTTP or HTTPS part of the URL. But do you know how it is related to port 443? If not, read on to find out about what this port is, what it does, and how to enable it.
Table of Contents
Table of Contents
What is port 443?
Port 443 is a virtual point through which data transmissions are sent and received. This communication endpoint is used by transport layer protocols, like the Transmission Control Protocol (TCP), to divert different types of web traffic to its destination.
Whenever you are browsing the internet, your computer connects with a server that hosts the information and gets it for you. To establish this connection, there needs to be a port through which the traffic can travel.
All network ports are numbered. For example, port 80 handles all unencrypted web traffic, while information that travels through port 443 is encrypted and, therefore, secure while in transit. Ports are also associated with network protocols that are either HTTP or HTTPS. But how are these two different and what makes HTTPS the more popular choice among website owners?
How does HTTPS work?
The Hypertext Transfer Protocol Secure (HTTPS) uses the Transport Layer Security (TLS) certificate (a more recent version of the SSL certificate, though these terms are used interchangeably) to secure the communication between a client and a server. TLS does that by encrypting the communication channel between the browser and the web server. If the website you’re visiting is secured with the TLS encryption, this will be represented in the URL bar as HTTPS, where “S” stands for “secure,” and a padlock symbol in the beginning of the address.
When a browser sends a request to a website, all information that is transmitted using HTTPS, like your login details, stays encrypted. If a hacker tries to read this information, they won’t be able to make heads or tails of it because they will only see a scrambled, unreadable text jumble. This is because the data goes through an encryption algorithm that generates a ciphertext, which is unreadable to an outsider without a decryption key.
This encryption also prevents your internet service provider (ISP) and other third parties from eavesdropping on you or intercepting communication between your browser and the website’s server.
To establish a secure connection, HTTPS uses port 443, which is the default port for HTTPS traffic. In fact, most secured sites use port 443 for data transfers. But what exactly does HTTPS port 443 do?
What does HTTPS port 443 protect?
HTTPS over port 443 is used for the transmission of secured traffic, thus creating a secure communication channel between the client browser and the server it wants to connect to.
This channel secures the sensitive data that you provide when you pay for goods or services online, such as your login credentials, credit card information, or bank account number. This is why an HTTPS connection over port 443 is commonly used by online businesses and financial services that aim to protect users from data breaches and secure their sensitive information.
Why do we need port 443?
We need HTTPS port 443 because it allows secure HTTPS connection and transmission of encrypted data. When data is exchanged via a regular port, such as port 80, it is visible in plain unencrypted text. This is risky, because snoopers and hackers might see and intercept traffic data.
With the expansion of e-commerce, data protection has become a priority. Any website owner, who wants their clients to use their services securely and to be trusted, will use an encrypted connection for data transferred between their clients’ browsers and the web servers that host their websites. This is where HTTPS port 443 becomes indispensable. So let’s see how you can enable it on your computer.
How to open port 443?
Here is how to open port 443 on Windows and Mac.
To enable port 443 on Windows, you will have to add it to Windows Firewall. Follow the steps below for a smooth process:
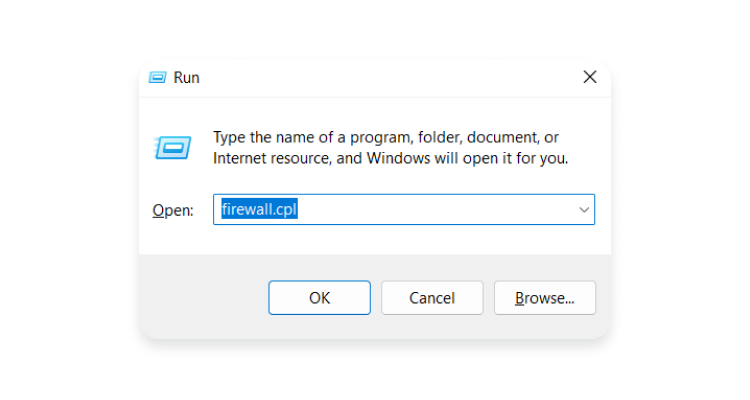
- Open the Firewall control panel by accessing “Start” > “Run,” then type in:
firewall.cpl

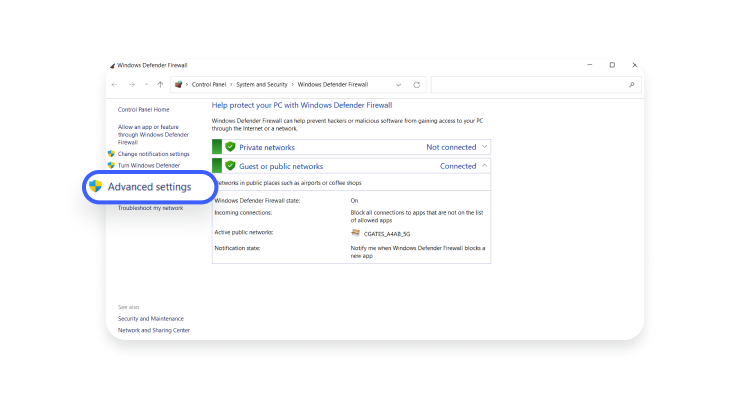
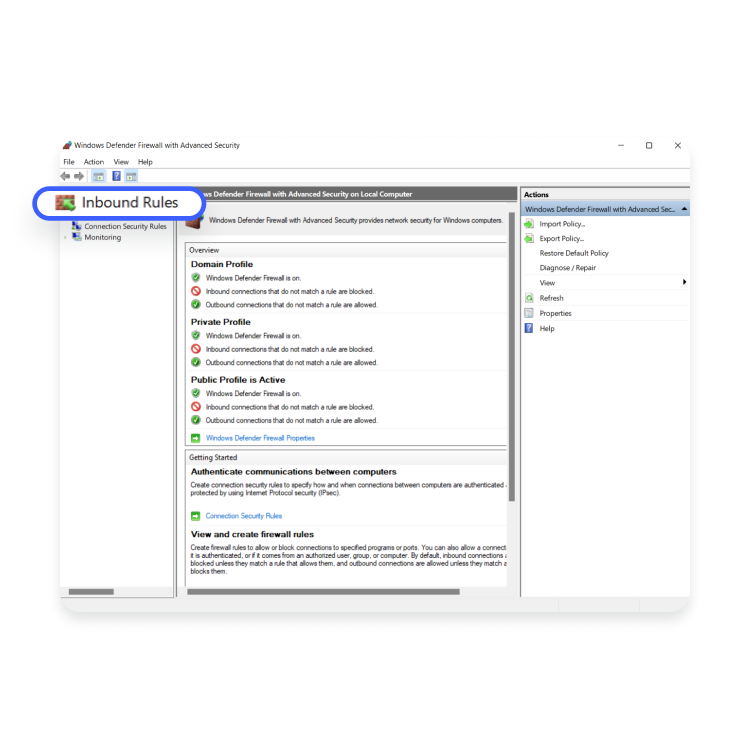
- On the left pane, select “Advanced settings” and click on “Inbound rules” in the top-left corner.


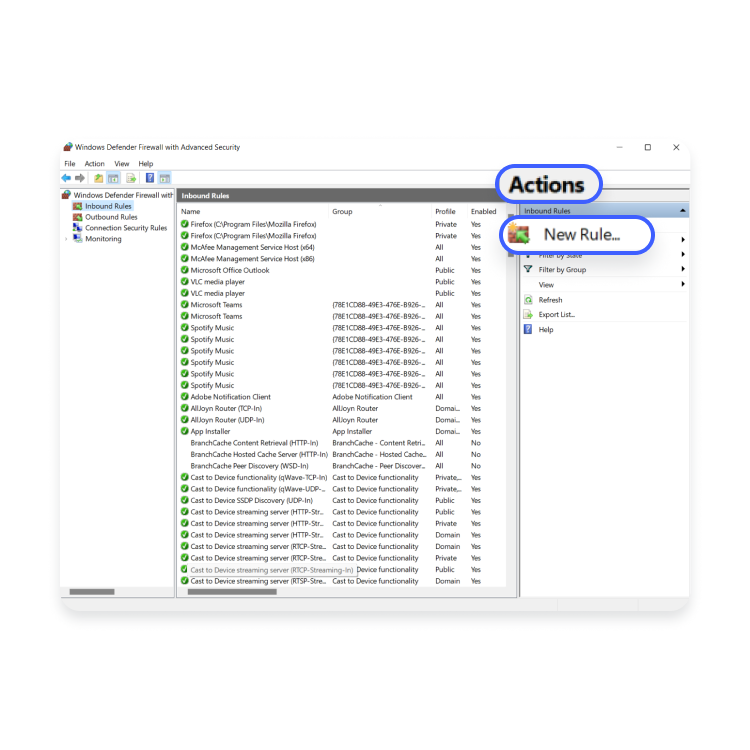
- Then, click on “New rule” on the right-side panel in the “Actions” column.

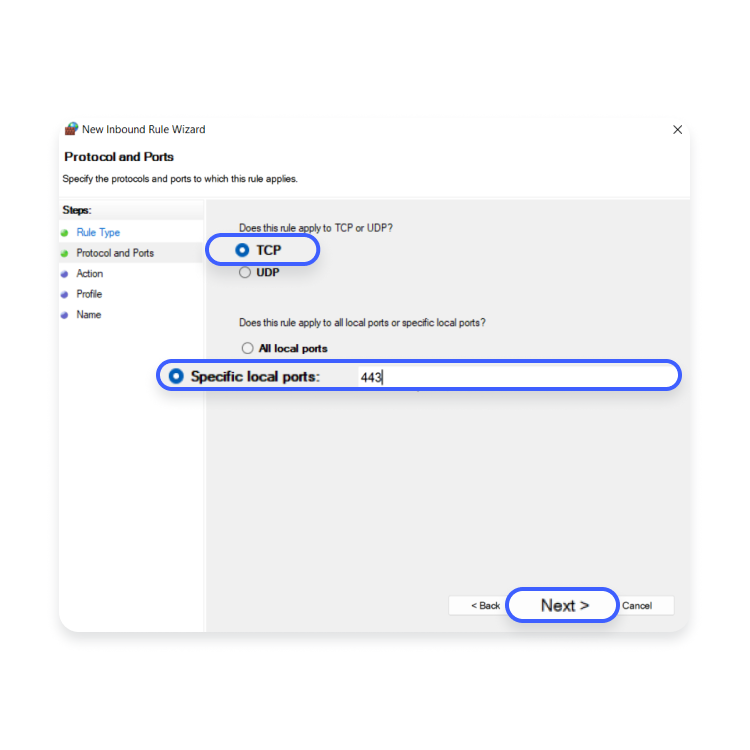
- A new window will open. Select “TCP” > “Specific local ports,” and type in “443” next to it.

- In the “Action” window, select “Allow the connection” and click “Next.”

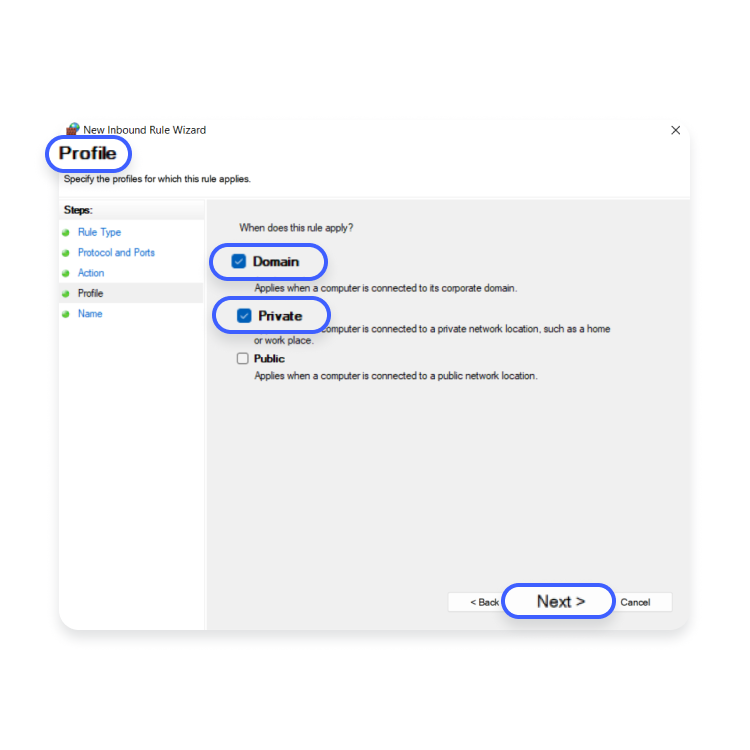
- In the “Profile” window, choose “Domain” > “Private,” and click “Next.”

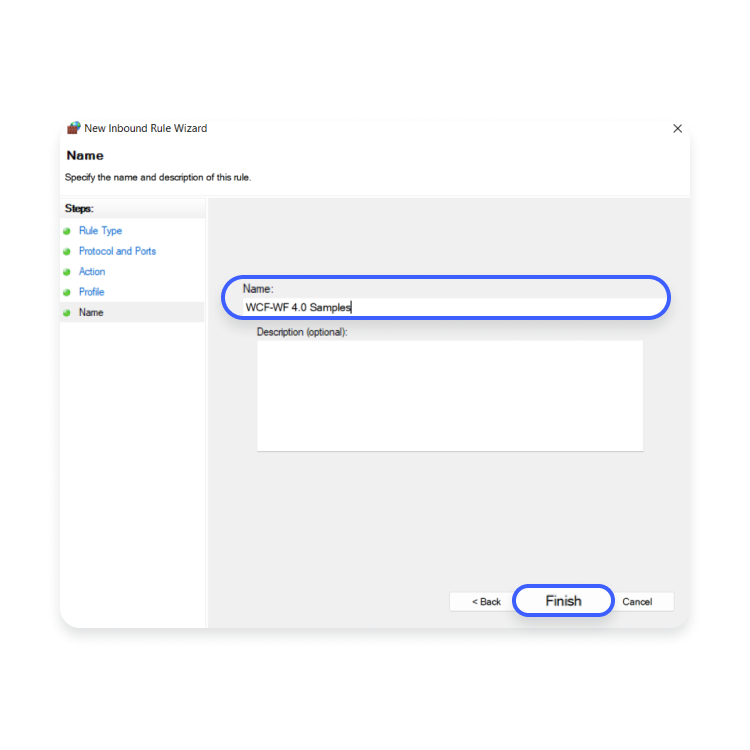
- In the “Name” window, type in “WCF-WF 4.0 Samples” and click “Finish.”

And below is how you can enable port 443 on Mac OS. But before you begin, make sure your firewall is disabled (it should be by default), then follow the steps below:
- Open the “Terminal” app.

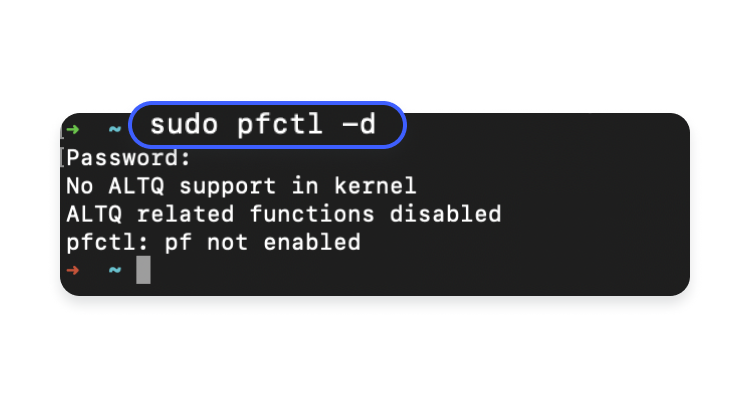
- At the prompt, enter the following command to stop the packet filler (pf) firewall in case it’s active:
sudo pfctl -d

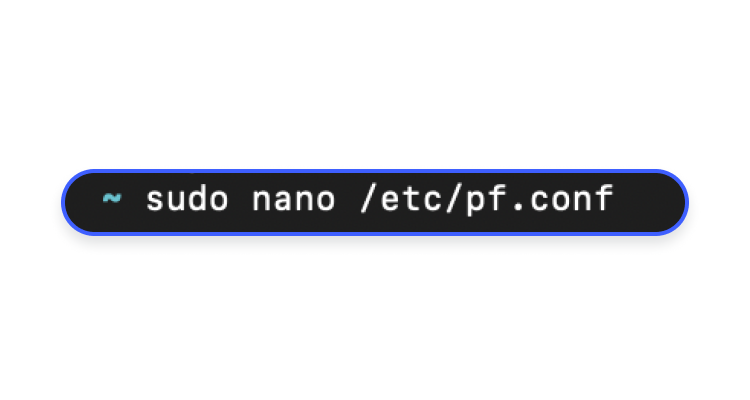
- Open the configuration file for “pf” by using the “nano” text editor:
sudo nano /etc/pf.conf

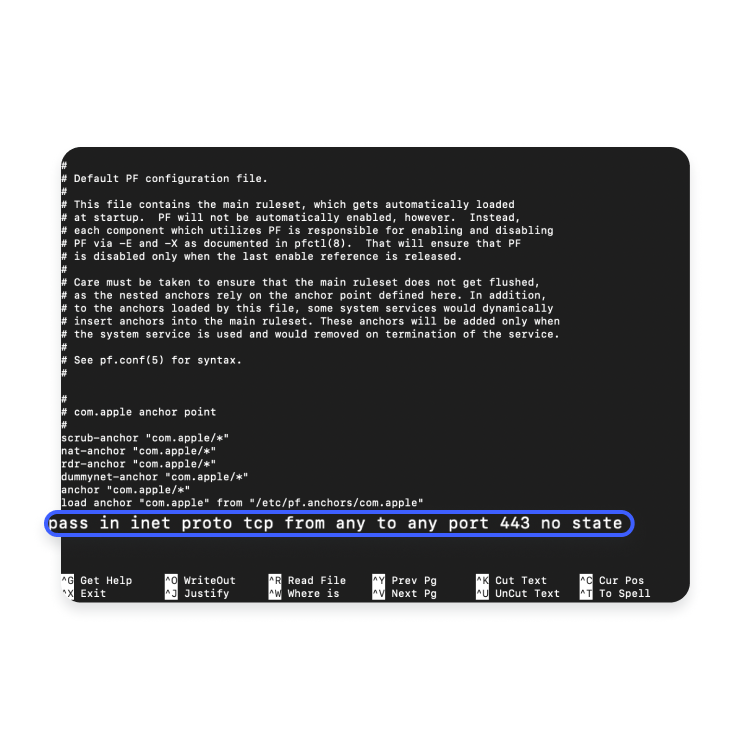
- In the text editor, add your custom rules at the bottom of the file.
- To open port 443, enter the following command at the bottom of the file below the existing configuration:
pass in inet proto tcp from any to any port 443 no state

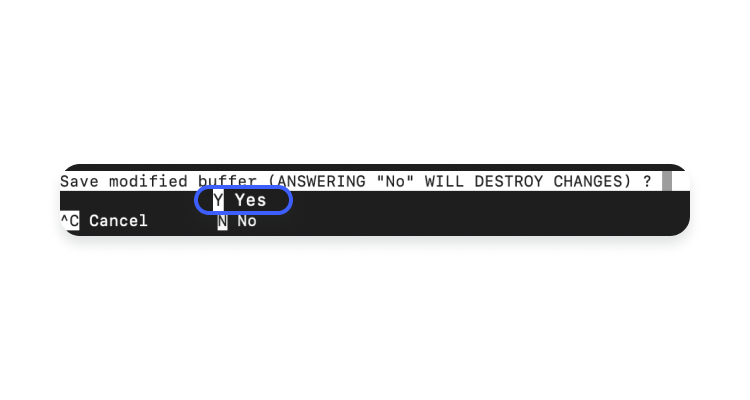
- Press “Ctrl-x” to exit “nano,” and press “Y” and “Enter” to confirm that you want to save the file with the same name.

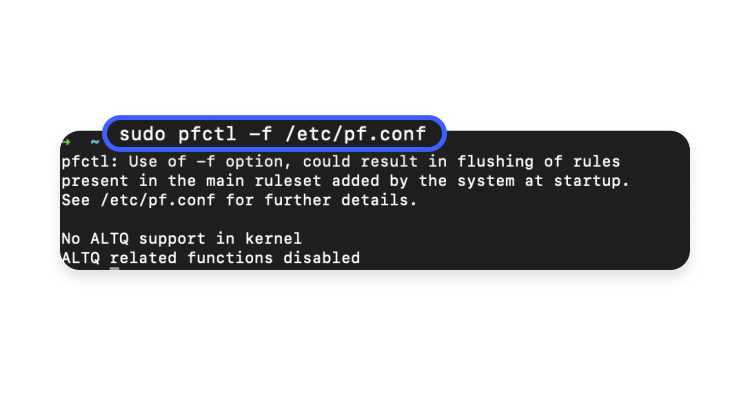
- Reload the firewall’s settings:
sudo pfctl -f /etc/pf.conf

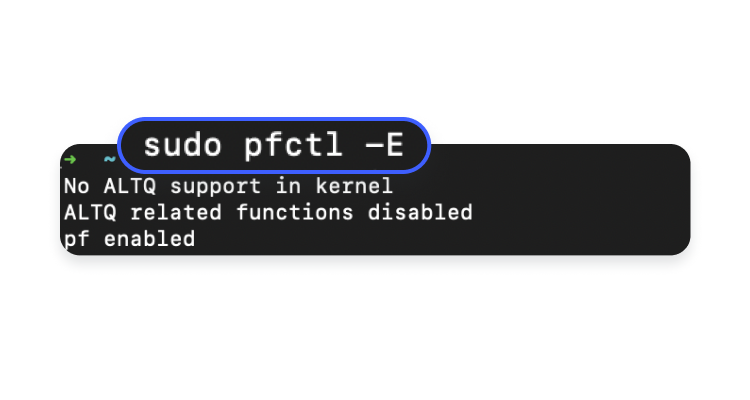
- Finally, restart the firewall:
sudo pfctl -E

TLS/SSL Handshake process
An TLS/SSL handshake process is a form of communication between a client’s browser and a server where the two decide what protocol version will be used for further communication. How does performing a TLS handshake work in practice?
- The browser sends a “hello” message to a web server it wants to communicate with. It includes the SSL/TLS version (encryption algorithms) the browser can support.
- The server responds with a “hello” message with its SSL certificate and public key. The browser and the server use asymmetric cryptography to exchange secure messages. This means that the browser needs the server’s public key to encrypt the messages, and the server needs two keys – private and public – in order to decrypt it. No third party can decipher these messages.
- The browser then uses the server’s public key to create a pre-master secret and sends it to the server. This will be used to create session keys and elevate the communication to symmetric encryption. Both parties will now be using private keys only. Symmetric cryptography will make their communication much faster and will use less resources.
- The server decrypts the pre-master, uses it to create a symmetric key, and exchanges it with the browser. With symmetric encryption in place, they can now exchange encrypted communication. Website traffic has been secured.
Want to read more like this?
Get the latest news and tips from NordVPN.