Key takeaways:
- Malicious websites are designed to harm your device and steal your data. Often, they do this through phishing or malware attacks.
- If you visit a malicious website, your personal data or device could be at risk, especially if you interact with it or download files from the site.
- To spot malicious websites, look for suspicious URLs, fake security alerts, offers that seem too good to be true, unsolicited downloads or software prompts, minimal or fake contact information, misspellings, poor design, and fake security alerts.
- To protect against threats from malicious websites and minimize the risks, keep your software up to date, be careful with emails, turn off auto-play, enable a firewall, check URLs for malicious elements, and report malicious websites. Also, consider using NordVPN’s Threat Protection Pro™.
What are malicious websites?
A malicious website is a web page designed to harm visitors and their devices and steal their data. These sites often use social engineering techniques like phishing, where cybercriminals trick you into giving away sensitive information like passwords or credit card details. Fake websites that contain malicious code might also spread malware — dangerous software that can steal your data, spy on what you’re doing, or even take over your device.
How common are malicious websites?
Malicious websites are becoming more common and are a growing threat to everyone online. The AV-TEST Institute reports that over 450,000 new malicious programs are detected every day, showing how fast these dangers are spreading.
Phishing attacks, which are often launched through these harmful sites, are also on the rise. In 2023, phishing attacks surged nearly 60% globally, according to the Zscaler ThreatLabz 2024 Phishing Report. The situation in 2023 was so severe that the Anti-Phishing Working Group (APWG) called 2023 "the worst year for phishing on record."
The APWG also reported that unique phishing email campaigns increased by 64% in the first quarter of 2024 compared to the fourth quarter of 2023. This sharp rise in phishing websites suggests that phishers are becoming more sophisticated. These cybercriminals often change their email subject lines to bypass spam filters and reach your inbox.
These findings show that it’s becoming increasingly challenging to identify phishing emails that could lead to malicious websites. It’s now more important than ever to be cautious with unexpected messages, even if they appear to be from familiar sources.
Are you in danger if you have visited a malicious website?
If you visit a malicious website, several things could happen that put you at risk: your device might get infected with malicious software (especially if your operating system or browser has vulnerabilities), your personal information could be stolen, or you might be tricked into giving away sensitive data.
Whether you’re already in danger depends on what happened during your visit. If the website contained malicious code, it could have automatically installed malware, putting you at risk from viruses, ransomware, or spyware that can steal your information or compromise your system. Even if nothing seemed to happen, the site might have secretly installed harmful software in the background by exploiting vulnerabilities in your browser. This hidden installation process is known as a "drive-by download."
However, if you quickly closed the malicious website, ran a security check, and didn’t enter any sensitive information, you’ve probably minimized the risk. By not interacting with the site or sharing personal data, you avoid the main dangers these malicious websites present. Still, it’s important to stay cautious. A complete security scan will help you detect and remove any hidden malware that you may have downloaded.
How to recognize a malicious website
To spot malicious websites, you need to stay sharp. While some fake websites are easy to recognize, many malicious websites have become more sophisticated and look convincingly real. Here’s how to identify a malicious website:
Suspicious URLs. Be cautious of URLs with extra words or characters, like “https://google.something.com,” which could indicate a subdomain of a malicious website. Also, look for slight changes in well-known domain names, such as “https://faceb00k.com,” where letters are replaced to imitate legitimate websites.
Fake security alerts. Be wary of websites that suddenly claim your device is infected with malware or that your software is outdated, especially if you didn’t initiate a scan.
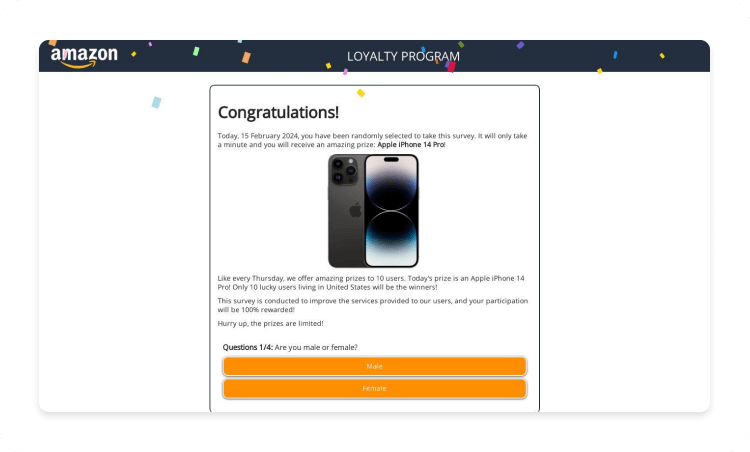
Promises of fake prizes. If a site claims you’ve won a prize and asks for personal information to claim it, it’s likely a scam.
Unsolicited downloads or software prompts. If a site unexpectedly asks you to run or download software, it’s a big sign that the website is malicious.
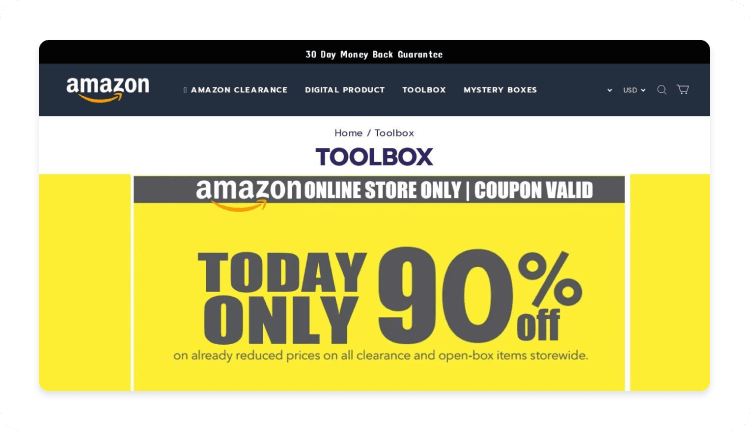
Overly generous deals. Offers that seem too good to be true, especially if they aren’t advertised elsewhere, are often a sign of a scam.
Minimal or fake contact information. If a site provides little to no contact details or the information seems fake, it’s probably untrustworthy.
Misspellings and poor design. Spelling mistakes, grammatical errors, or unprofessional design elements are clear red flags for a malicious website.
To go beyond spotting obvious signs and truly protect yourself online, learn how to check a website's safety step by step. If you're particularly interested in avoiding fake online shopping deals, you can also take a look at our guide on how to avoid fake shopping websites.
Examples of malicious websites
With cybercriminals becoming more adept at disguising malicious websites as legitimate ones, many people have fallen victim to phishing and malware attacks. The following malicious website examples highlight how these phishing sites have tricked people into revealing their sensitive information.
Bahamut group fake news websites
The Bahamut cybercrime group is known for creating fake news websites that closely resemble legitimate sources. These malicious sites redirect victims to phishing pages designed to steal login credentials for platforms like Google, Yahoo, Microsoft, and Telegram.
In one case, the group took over the domain of an information security news site and repurposed it to promote content on geopolitics and industry news. To appear legitimate, Bahamut used fake contributor profiles featuring the names and photos of real journalists. The group also set up social media accounts and other websites to support this illusion of credibility.
The group also distributed malicious mobile apps through these phishing sites. Once downloaded, these apps created backdoors on victims' devices, allowing Bahamut to track their activities, access their files, and monitor their locations (BlackBerry, 2020).
APT28 (Fancy Bear) fake government websites
APT28, also known as Fancy Bear, is a Russian cyber espionage group infamous for creating fake sites, including webmail login pages that closely mimic legitimate websites of government bodies and political organizations. To attack its victims, APT28 typically employs both phishing messages and credential harvesting.
During the 2016 U.S. presidential election, APT28 targeted the Democratic National Committee (DNC) with a phishing campaign involving a fake webmail login page. This tactic allowed the group to gain unauthorized access to sensitive information, which played a key role in its broader cyber-espionage activities.
Equifax data breach copycat sites
In 2017, a data breach at Equifax, a leading credit bureau, exposed the personal information of nearly 150 million people, making it one of the biggest data breaches in history. In response, Equifax set up a settlement claims website two years later.
However, cybercriminals quickly took advantage of the situation by creating malicious copycat websites. These phishing websites were designed to steal personal information from unsuspecting individuals who believed they were submitting legitimate claims related to the breach (Equifax, n.d.)
How to keep yourself protected from malicious websites
Malicious websites, especially those distributing drive-by downloads, are a growing online threat. By taking the proper precautions, you can protect yourself and browse the internet with confidence.
- Keep your software and operating system up to date. To fend off threats, ensure that your operating system, browser, and antivirus software are up to date. Software updates often include security patches that address vulnerabilities discovered since the last update. Although you may be tempted to click “remind me later,” installing security updates as soon as they become available is the best practice.
- Use antivirus software. Install and regularly update antivirus software to protect your device from online threats, specifically those posed by malware sites. This software actively scans your device, detecting and blocking viruses, malware, and other harmful activities before they can cause any harm.
- Be careful with emails. Don’t open suspicious emails, especially if they contain attachments or come from unknown senders. If you’re unsure about a link, type the website address directly into your browser. By typing the URL yourself, you avoid the risk of being redirected to a malicious site.
- Turn off auto-play. Go to your browser settings and turn off the autoplay function. This action will neutralize any content that relies on video plugins. It’s a simple way to prevent drive-by downloads and limit your exposure.
- Enable a firewall. A firewall acts as a barrier between your device and the internet, filtering out potentially harmful connections from malicious websites. By monitoring incoming and outgoing traffic, a firewall helps prevent unauthorized access and stops dangerous content from reaching your system.
- Use Threat Protection Pro™. NordVPN’s Threat Protection Pro™ feature includes a malware blocker that automatically blocks dangerous sites, malicious redirects, and harmful ads and scans files during downloads to prevent malware attacks.
- Check URLs for malicious elements. As a free alternative to our Threat Protection Pro™ feature, consider using a link checker that scans any URL you wish to visit. This tool can help detect malicious URLs, malware, phishing attacks, botnets, and fake websites.
- Report malicious websites. If you visit a malicious website, report it to your browser, search engine, or a cybersecurity organization. Reporting these sites helps prevent others from falling victim and allows authorities to take down these threats more quickly.
Online security starts with a click.
Stay safe with the world’s leading VPN