The Enigma machine: How cryptography and social engineering helped win WWII
The Enigma machine was a device that created encoded messages, specifically to protect wartime communications. Its creation was a result of wartime necessity, because the Germans had already created a powerful machine to protect their secrets. The Allies needed to catch up with something of their own.
In creating the Enigma machine, the Allies helped to defeat one of the greatest evils the world has ever seen and created the precursor to the modern computer. Even now, almost a century later, there are still lessons we can learn from the Enigma machine about modern cybersecurity.
What follows is the fascinating story of how clever spies, daring commandos, brilliant mathematicians, and industrious engineers came together to crack Germany’s Enigma code machine…
What is the Enigma machine?
The Enigma machine was a keyboard that scrambled messages in a way that could only be unscrambled by someone using an identical machine with identical settings somewhere else. It was initially created for commercial and diplomatic use before the war, but the government later began developing versions with more powerful encryption exclusively for the military.
The machine looked like a typewriter, but instead of typing out letters on a sheet of paper, it had a board of lights with one light for each letter of the alphabet. As the operator typed each letter of their message into the machine, a letter on the board would light up to produce, letter by letter, a scrambled message.
The German military used the Enigma code to great effect during WWII. Their seemingly unbreakable encrypted messages would direct army movements, aircraft raids, and the deadly U-boat submarines that terrorized Allied military and civilian ships on both sides of the Atlantic.
Cracking the Enigma machine was key to gaining an advantage in WWII. But first, they had to figure out how it worked.
How did the Enigma machine work?
The key to its power lay in the clever way that the inside was wired. The wartime Enigma could create trillions and trillions of potential combinations – too many for any contemporary methods to crack.
When it came to the functionality of the Enigma machine, the main input device looked similar to a typewriter. The keys were then routed into a collection of rotating wheels and a plugboard. The combination of the wheels and plugboard meant whatever message was output would be scrambled.
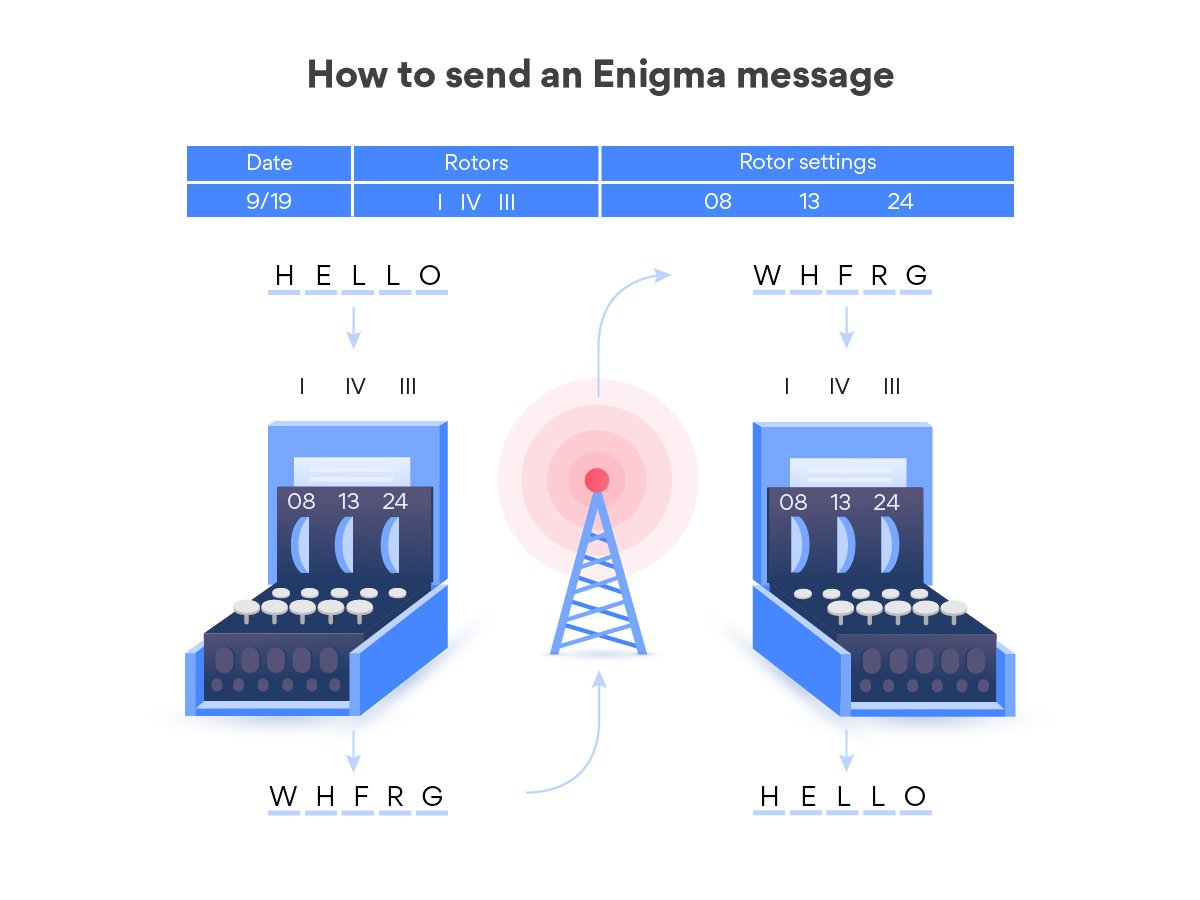
Let’s see what you’d have to do to create and send an Enigma-encrypted message:
How Allies sent an Enigma-encrypted message
Sending a message through the Enigma machine was no simple matter. Several procedures needed to be properly observed before using the machine.
Checked the settings
The Enigma machine only worked if both ends of the conversation were using the same settings. To this end, the German military would issue sheets of daily Enigma settings that would be replaced at various frequencies – usually once a month.
The Enigma was constantly updated throughout the war, so the exact types of settings varied. However, they usually included:
- The rotors. The Enigma M1 had three rotors that the operator could choose from from a pool of five, though this number was later increased to eight (and a machine with four rotor slots was released toward the end of the war).
- The rotor positions. Each rotor was a gear with 26 positions – one for each letter of the alphabet. The starting position for each rotor would change every day.
- The “Stecker” pairs. At its strongest, the military Enigma machine had a switchboard that would allow the operator to create letter pairings. They were instructed to select 10 pairs each day, and when they did, those letters would be switched, further scrambling the message.
Every Enigma also had a reflector, but only a few of the versions could adjust their reflectors. We’ll get to the reflector later, because it introduced a flaw that was crucial to the Allies’ efforts to crack the Enigma.
In any case, once the Enigma machine was correctly configured, it was time to send the message.
Typed and recorded the message
The Enigma was not a transmission device, it was an encryption device. As you typed in a message, it would light up the letter that each of the letters had been scrambled to. It was the operator’s job to write down the message and transmit it. With each key click, the rotors would advance, changing the settings.
Unscrambled the message
At the other end, the operator would type in the scrambled message and record the letters that lit up on their keyboard. When they finished writing down the letters, they’d spell out the message that was sent. Anyone intercepting it would be left with gibberish.
Now that we know how it was used, what made the Enigma so powerful? Why was it such a phenomenal challenge for the Allies to crack the Enigma’s code?
Enigma was so hard to crack with contemporary means because the settings changed with each keystroke. If you were to sit down at an Enigma machine right now and press the “A” key three times, you would get a different scrambled letter every time. As an example, the word “AARDVARK” could very well be scrambled into “GFKLRLWC” – and if I were to type it again later in my message, it could look completely different!
It’s hard to convey just how deeply scrambled any given code could be because the numbers are truly astronomical. Hopefully, the math here will help:

Brute-forcing the Enigma was effectively impossible. So how could the Allies possibly hope to break it?
Well, the Enigma itself had one fatal flaw – the reflector component made it so a letter could never be encoded to itself in the scrambled message. In other words, if the scrambled text is “HWLER”, you can immediately rule out the word “HELLO” in that spot because the “H” and the first “L” would match. But to really understand why this was such a key flaw, we need to see first how the Allies worked to break the Enigma.
Codes, codebreaking, and war
The element of surprise is crucial in war. Intercept an enemy’s message and you’ll know their moves before they do. World War II was no exception.
Radio waves enabled the nations fighting in WWII to communicate with their troops over vast distances. However, it was easy for enemies to hear those messages as well. In a war where everyone can hear what you’re saying, you need to speak in codes to transmit secret information. This was why the German government developed the Enigma machine.
How was the Enigma code cracked?
Hollywood has shown us how the British military eventually took the initiative in cracking the Enigma code, but every Allied country pitched in to help. The Enigma code breaking process began long before the war broke out.
The combined efforts of some of the most gifted mathematical minds helped crack the enigma. Through innovations discovered by Alan Turing and Gordon Welchman, a logic-based device was created to help decipher the Enigma.
Watch our video about the story of cracking the Enigma machine.
Poland begins the work
As Germany’s neighbor, Poland understood the threat Germany presented and began attempting to crack the Enigma’s earlier and simpler versions.
Before the war, Poland faced weaker Enigma encryption and shoddier German security practices. However, the dire international need to decrypt it was not yet present and Poland did not have the resources or information available to make the breakthroughs that their allies did later.
Impressively, some of Poland’s greatest breakthroughs came through the power of math and deduction.
- Polish mathematician Marian Rejewski made accurate deductions about the inner workings of the Enigma based entirely on mathematical analysis. He helped invent the first cryptographic machines designed to crack Enigma messages, and these machines later inspired the British to adopt a similar approach.
- Polish mathematician Henryk Zygalski invented meticulously perforated paper sheets called Zygalski sheets that were used to determine rotor settings. His insights also helped kickstart British cryptography efforts.
The Polish mathematicians achieved remarkable results. They proved that the earlier versions of Enigma could be cracked and provided the theoretical foundations upon which many of the Brits’ later breakthroughs were built.
As the war approached, the Allies began sharing intelligence to accelerate the cracking of the Enigma. Brief secretive meetings were arranged at hotels and train stations across Europe to exchange information. A French spy named Hans Tilo-Schmidt who was embedded in the German Armed Forces’ Cipher Office produced many useful clues. For years, he sold Enigma manuals and other info to French intelligence that made its way to the rest of their allies.
The British take the lead as the war begins
In 1939, Germany invaded Poland, beginning World War II. The Polish mathematicians fled across several countries, finally making it to the UK, where they shared everything they knew with British intelligence. However, they were tasked with solving other cryptographic puzzles – Britain and the US took over Enigma decryption and shrouded it in the highest levels of secrecy.
As the war approached and got underway, a few significant changes occurred:
- The Enigma became stronger. Germany was quite confident in the Enigma machine, but they also knew that they had entered a cryptographic arms race. Over the course of the war, the German Enigma machine helped the army improve its communication procedures and made the machines themselves more secure. They increased the number of rotors and the number of letters that could be paired on the plugboards.
- The Allies had more to work with. Messages were being sent every day to active military units around the world. With the greater resources at the British government’s disposal, they could analyze vast quantities of encrypted messages to search for patterns, weaknesses, and mistakes.
Scores of brilliant mathematicians, analysts, and engineers worked at the top-secret facility at Bletchley Park, but Alan Turing and Gordon Welchman are considered the stars of the Enigma effort. They are credited with developing the bombe – an electro-mechanical calculator that helped crack the Enigma and that many call the precursor of the modern computer. With that said, their contemporaries have said that the contributions of the Polish mathematicians saved Turing and Welchman a year of work.
Let’s break down the steps in the British Enigma code breaking process so we understand how it works.
1. Hunting for clues. Soldiers would search enemy command posts for code books. Radio operators would record scrambled messages and analyze their patterns. Sailors would scramble to search captured or wrecked ships for surviving code sheets. Spies sought out technical information or other ways to undermine the Enigma project. The information they gleaned from different sources helped the Brits understand the Enigma and how it was used.
2. Cryptanalysis. Teams of British mathematicians analyzed the messages to find patterns and clues that would help, but their most useful tools were cribs – plaintext words they hypothesized might exist in a given scrambled message. To produce useful cribs based on solid hypotheses, clever cryptanalysts had to pore over mountains of data gathered from across Europe by the Brits and their allies. The reflector flaw mentioned earlier made these cribs much easier to use. The location of a crib in the text could be ruled out if even one of the letters matched the scrambled text.
3. Computation. Once they had good cribs and intercepted encrypted messages, the analysts at Bletchley Park could use their bombes to test the cribs and discover the Enigma settings being used by the Germans for that day. If they could do so fast enough, they would have the power to unlock Enigma messages for the rest of that day. Each day they had to start all over again.
Each bombe machine was essentially composed of a large array of simulated Enigma rotors. They worked by testing thousands of Enigma settings to discover settings that could have produced the cribs that the analysts fed into them. With clever insights, the analysts were able to rule out certain settings to make the machines’ work more efficient.
Eventually, the Brits were able to manufacture vast facilities full of bombe machines and set them to work to crack the Enigma codes. Towards the end of the war, the British had 155 three-rotor bombes operating across multiple sites (to protect them from air strikes).
Let’s go over the clues and the human mistakes that enabled the British mathematicians to form useful cribs to feed to their bombe machines.
The human weak point
Many modern historians, mathematicians, and cryptanalysts agree – if the Enigma code had been operated perfectly, it may have remained impossible to crack. However, it wasn’t. The British relied on the humans operating the Enigma to make mistakes that could give them clues. Here are just some of the ways that the people using the system actually undermined it:
- Repetition. Some of the most easily exploitable cribs came from daily reports where formats rarely changed. Most U-boats, for example, would send daily weather reports. Analysts could make educated guesses at the location of the plaintext word “weather report” in the scrambled message. In less-active regions, military units might often send messages that contained the words “nothing unusual” or “nothing to report” – another frequent repetition that the British used to great advantage.
- Unsecure duplication. In some cases, a message would travel one leg of its journey encrypted via Enigma, get decrypted, and continue its journey with a weaker cipher or no encryption at all. These weaker messages were a valuable source of cribs for solving that day’s Enigma settings.
- Poor setting sheets. By poring through their data, analysts made discoveries about how the Enigma setting sheets were made. In some areas, for example, no rotor settings could ever be repeated in a month, so once they had been used, they could be ruled out for upcoming days. In others, no rotor could occupy the same slot in the Enigma as it had the previous day, also reducing the number of options analysts needed to check. In other cases, some commands would recycle entire rows or columns of the previous month’s sheets, handing the British small victories when these flaws were detected.
- Short messages. The longer an Enigma message was, the more resistant it would be to analysis. The use of short messages gave analysts clues as to what might be in them.
- Overconfidence. There were periods during the war when the British managed to break Enigma codes for weeks on end, safely directing their ships around German U-boat patrols. Still, up until after the end of the war, German commanders still believed that the Enigma was only breakable in theory, but not in practice. Sometimes, the British took measures to perpetuate this misconception. In one case, when the location of a U-boat in the Mediterranean was discovered by cracking an Enigma message, the British air force first sent a scout plane to the location to “spot” the submarine and provide a plausible pretext for attacking it.
Why was the Enigma machine so hard to crack?
The Enigma code had a complex encryption method. The cipher settings would alter with each new keystroke, using different wheels and rotations to create seemingly random codes. While the work of the mathematicians can’t be denied, the Germans made several mistakes that helped the Allies divine the cipher of the day.
There were also some interesting specific scenarios or events that gave the Allies plenty of clues to work with when cracking the Enigma.
The “LLLL” message
German operators sometimes sent decoy messages to delay British efforts to crack their encryption. On one occasion, however, a British analyst noticed something strange – the scrambled message he was inspecting contained absolutely no “L” letter anywhere in the text. Because of the reflector flaw, this meant that any or all of the letters could be “L.” It turned out that it was all of them – the lazy German operator had simply mashed the “L” button on his Enigma to write his decoy message, practically gifting the British the settings for that day.
Double agent Nathalie Sergueiew
Nathalie was a German spy who worked with the British intelligence as a double agent. Her primary contribution to the Enigma effort was to send verbose reports back to her German commanders that were later re-encrypted using the Enigma. This provided British analysts with excellent cribs for discovering machine settings when her messages were relayed.
The sinking of the U-559
The German Navy distributed setting sheets written in ink that would dissolve when wet, making them highly resistant to capture. At one point in the war, they also upgraded their Enigmas to use four rotors, making them much more difficult to break.
The first great breakthrough in cracking the upgraded Enigma was achieved in a daring hunt by the destroyer HMS Petard. An engagement with German submarine U-559 ended with the submarine’s surrender after dark had fallen. Nonetheless, the captain immediately ordered three soldiers to dive into the water. Illuminated by spotlights, they swam to the U-boat as its crew surrendered. They were tasked with retrieving any books they could before it sank. Fortunately, the submarine sank slower than it should have due to mistakes made by the departing crew. This gave the soldiers the precious moments to retrieve their valuable prize – intact codebooks.
Operation Claymore
During a daring and explosive raid on German industrial facilities on the Lofoten islands, the commandos seized an unexpected prize – a set of Enigma rotors and a codebook from a docked ship.
These are just a few select colorful cases. This parallel cryptographic arms race was fought throughout the war right up until the end. There was no point during the war when either side could be said to have fully won or lost the cryptographic battle, but there were some stretches of time during which the Allies enjoyed nearly unrestricted access to German radio communications.
The war was won by more than just the breaking of the Enigma, but uncovering the enemy’s operational secrets no doubt played a pivotal role. Furthermore, this retelling has been simplified to touch on the key elements that can be useful for modern online security. For those interested in mathematics, cryptography, or the history of WWII, there is much more to this story available online!
What we can learn from the story of the Enigma
For our purposes, there were two significant outcomes of the struggle over Enigma encryption in WWII:
- Significant advances in cryptography. The development and subsequent breaking of the Enigma code advanced cryptographic understanding by leaps and bounds. The mathematicians and analysts worked with many of the principles that we use in cybersecurity today – and they encountered many of the initial bugs that our modern tools attempt to solve.
- Significant advances in computing. The bombe machines inspired by the Polish and developed by the British were electromechanical computers. Many consider them to be precursors to the modern computer. They were capable of accepting user inputs, performing calculations that would have been unfeasible for humans, and computing solutions to a serious problem. The Brits made even further advances in computing when they built the Colossus, a computer designed to break the German high command’s Lorenz cipher. Though this encryption process was theoretically more powerful, it was also more vulnerable to analysis. The British codebreakers broke the Lorenz with math and analysis – without ever seeing the encryption machine itself.
While enormous, the advances in computing are beyond the scope of this article, so let’s stick to what we can learn about cryptography and cybersecurity.
1. Laziness leads to lax security
The Germans weren’t entirely wrong in their belief that Enigma was unbreakable by contemporary means – it may have remained unbroken if it was part of a perfect system, but it wasn’t. When some German commanders recycled their Enigma settings, that sounds a whole lot like when people today reuse their passwords across multiple sites – a big mistake!
2. Key security is as important as encryption power
Even with its built-in flaws, the Enigma exhibited impressive encryption power. However, other parts of the process weren’t nearly as secure. The setting sheets used by Enigma operators are an example of an unsecure shared key exchange that introduces vulnerabilities to the system. The keys (Enigma settings) changed daily, but the sheets could be captured or photographed, and they were created by people who sometimes took shortcuts.
Today, we have processes like the Elliptic Curve Diffie-Hellman key exchange, which allows parties to exchange secure keys over unsecured connections and to change those keys with every connection they make.
3. Secure systems require vigilant users
The technology behind Enigma was sound, but the system was only as secure as its users let it be. There are tons of tools out there to keep you safe, like VPN services, ad blockers, and spam filters. However, it’s up to each and every one of us to stay vigilant and informed about cybersecurity threats so we don’t undermine our security tools.