What is the Address Resolution Protocol (ARP)?
The Address Resolution Protocol is a fundamental part of any network, enabling communication between its devices. Naturally, it’s also a potent target for attackers who want to disrupt your network’s operations. But how does the Address Resolution Protocol work, and how can hackers compromise it? Let’s discuss the ARP process, types, attacks, and their prevention, starting with the meaning of the Address Resolution Protocol (ARP).
Contents
What is the ARP?
Address Resolution Protocol (ARP) meaning
The ARP, or “Address Resolution Protocol,” is a communication protocol that uses the device’s Internet Protocol (IP) address to discover its hardware address within the local area network (LAN). The ARP operates primarily at the data link layer of the Open Systems Interconnection (OSI) model.
The ARP is a request-response protocol – devices interact by initiating a request and expecting a corresponding response. In the case of the ARP, a device knows an IP address and requests a matching physical address, also known as the media access control (MAC) address, in a local network.
These IP and hardware address pairs, or IP-to-MAC mappings, are then available in ARP tables maintained by network devices, such as computers and routers.
How does the Address Resolution Protocol work?
The ARP process includes multiple steps:
- Request. A device (let’s call it Device A) wants to communicate with another device (Device B) on the same network. Device A knows the B’s IP address but not its hardware address. So, Device A sends out an ARP request – it broadcasts a message to all devices on the network, asking which device the IP address belongs to.
- Response. Device B responds to device A with its MAC address.
- Caching. Device A receives the response and stores it in its ARP cache. This cache is a table mapping IP and MAC addresses for future reference.
- Communication. Now that Device A knows the physical address of Device B, it can address data packets to Device B’s MAC address.
- Timeout. Device A can continue communicating with Device B by retrieving the latter’s MAC address from the ARP cache until the cache gets outdated or times out. Then Device A needs to send a new ARP request, and the process starts from the beginning.
What are the types of ARP?
“Regular” ARP covers the communication between devices on the same network. But sometimes, the ARP is needed for device configuration, solving IP conflicts, or communication among devices on different networks. That’s when different ARP types come into play.
Proxy ARP
Proxy ARP is a networking technique that includes a proxy responding to the ARP requests on the device’s behalf. Usually, a router acts as the proxy ARP on a network.
The proxy replies to the ARP query with its own MAC address. Once the device that requested the MAC address sends any data, the proxy forwards that data to the intended destination’s MAC address.
The device requesting the MAC address and the machine that the MAC address belongs to can be on different networks. With a proxy acting as an intermediary, devices can communicate even when they aren’t connected to the same network.
Gratuitous ARP
Gratuitous ARP is an ARP response not preceded by an ARP request. In other words, a device broadcasts its IP and MAC address pair without being prompted by another device.
Gratuitous ARP helps to check for potential IP conflicts. For example, a router checks if another device on the network hasn’t already occupied a particular IP address. Gratuitous ARP broadcasts also cue devices on the network to update their ARP tables.
Reverse ARP
Reverse Address Resolution Protocol (RARP) is a reversal of the ARP. Instead of knowing an IP and requesting the MAC address of another device on the network, the device knows its MAC and requests its IP address.
Reverse ARP translates the MAC address into the IP address, and the device requests its own IP address instead of asking for the address of another machine on the network. That’s why its applications are somewhat limited – you can use RARP for device configuration only.
Inverse ARP
Inverse ARP (InARP) is also a reversal of the ARP – instead of knowing an IP and requesting the MAC address, the device knows the MAC and requests the IP address.
The difference between the Reverse and Inverse ARPs is the device whose IP is requested:
- RARP: A device requests its IP.
- InARP: A device requests an IP of any other device on the network.
ARP vs. DHCP vs. DNS: What’s the difference?
ARP, DHCP, and DNS are all response-request protocols used on IP networks. But they serve different purposes.
- ARP maps the MAC address of a machine to its IP address on the local network. ARP comes into the spotlight when you want to send a data packet to another device on the local network, but you only know its IP address, not the MAC address.
- DHCP retrieves network configuration, including IP and DNS server addresses. DHCP automatically assigns an IP address to the new device you add to the local network, so you wouldn’t need to set an IP address for each device manually. It can provide other network configuration parameters, too.
- DNS finds the IP address of a website based on its domain name or URL. For example, when you enter “nordvpn.com” into your browser’s address bar, DNS translates this human-readable domain name into IP addresses that computers can identify.
When it comes to ARP and DHCP, we are talking about the local area network and the local (or private) IP addresses. DHCP is (usually) what assigns the devices with their IP addresses on the local network, and ARP translates those IP addresses into MAC addresses.
Meanwhile, DNS also works with global (or public) IP addresses outside the local network. DNS translates any domain name on the internet into its corresponding IP addresses.
(Read about the differences between private, public, and other types of IP addresses here.)
What is ARP in networking useful for?
ARP has many uses in networking, including:
- Address resolution and communication. The primary function of ARP is to map the IP addresses to MAC addresses within the same local network. It enables devices to communicate using MAC addresses, such as sharing files between devices or sending a document from your computer to a printer.
- Address conflict detection. You can use ARP to identify network address conflicts by checking the ARP cache on your device. It prevents communication disruption, unpredictable or failed responses, and data consistency issues.
- Address spoofing prevention. Identifying IP conflicts prevents malicious actors from impersonating legitimate devices on your network.
- Address cache management. The ARP stores IP-to-MAC mappings in its cache to ensure accurate and efficient communication within a local network. It helps to retrieve MAC addresses faster and frees up bandwidth for other communications on the network.
- Network troubleshooting. Network administrators can monitor ARP traffic to identify connectivity issues.
What is an ARP spoofing attack?
ARP spoofing or ARP cache poisoning is a cyberattack when a hacker sends fraudulent ARP responses to the local network. Cybercriminals send their MAC address to respond to any given IP address of a device on the network. If the spoofing is not identified, they perpetrate various attacks:
Man-in-the-middle (MITM) attacks
Man-in-the-middle attacks aim to intercept the communication between devices on the network. Hackers respond to the ARP query with their hardware address and intercept any data packets meant for the device they impersonate. This type of ARP spoofing can lead to sensitive or confidential information theft.
Denial-of-service (DoS) attacks
Denial-of-service attacks aim to overwhelm the target device or network with traffic to disrupt normal operations.
In the case of ARP spoofing, DoS attacks usually involve a cybercriminal sending false ARP messages (ARP requests and responses) to the network. Network devices update their ARP cache, creating incorrect ARP mappings. It blocks data packets from reaching their destination and leads to network disruptions.
If hackers send a large number of fake ARP messages, it results in significant communication failures, network congestion, and overloaded network resources. This type of DoS is also called an ARP flood attack. It can sometimes exacerbate other network attacks, including MAC flooding.
Session hijacking attacks
Session hijacking attacks aim to gain unauthorized access to an ongoing user session. When successful, attackers impersonate the user and perform actions on their behalf.
Session hijacking is similar to IP spoofing, except the MAC and not IP addresses are spoofed. It functions like MITM attacks, except after intercepting the data packets, attackers modify them before sending data to the intended destination. This way, cybercriminals can inject malicious code, alter the messages, or redirect the unsuspecting device to dangerous websites.
How to detect ARP vulnerabilities
You can use data packet analyzers, ARP-poisoning detectors, or network troubleshooting tools to detect ARP vulnerabilities automatically. Or you can manually check ARP tables (ARP cache) and identify the threats.
Here’s how to detect ARP poisoning manually:
- Open the command line interface on your device (“Command prompt” on Windows or “Terminal” on macOS and Linux).

- Type in the command “arp -a” and click “Enter.”

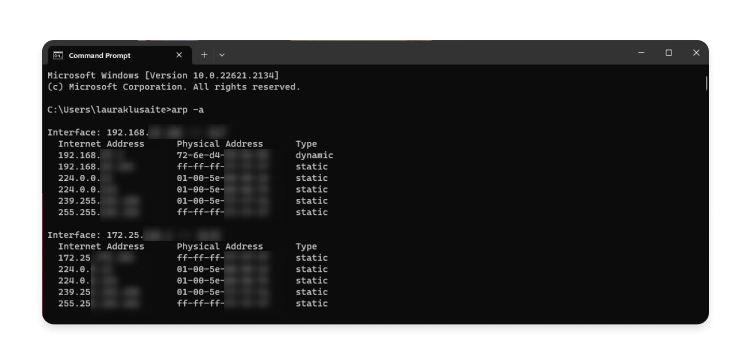
- You’ll see the table with IP addresses and their corresponding physical addresses. If multiple IP addresses are paired with identical physical addresses, your ARP cache may have been poisoned.

How to prevent ARP spoofing
It’s crucial to be proactive in securing your network to prevent ARP vulnerabilities and spoofing attacks. Here’s what you can do:
- Implement static ARP entries. Manually configure ARP entries on your network devices. This way, ARP mappings are fixed, and cybercriminals can’t manipulate them easily. However, static ARP involves a lot of manual work, so it makes sense for smaller networks only. Also, it prevents only simple ARP spoofing attacks.
- Enable ARP inspection. Many modern network devices support ARP inspection or ARP spoofing detection features. Enable them to monitor ARP traffic for anomalies and block or log suspicious ARP packets.
- Adjust ARP cache timeouts. The ARP cache timeout values are usually short, but you can set even shorter timeouts to reduce the window of opportunity for attackers to control ARP mappings.
- Monitor network traffic. Use network monitoring tools to continuously check network traffic for unusual patterns and unauthorized changes to ARP tables. They identify and respond to ARP attacks in real time.
- Partition your network into segments. Use routers or firewalls to isolate different parts of the network. This practice may not prevent ARP attacks entirely, but it limits their scope.
- Increase port security. Implement port security features to limit the number of MAC addresses allowed on each switch port. It can prevent attackers from connecting unauthorized devices to your network.
- Secure network access. If cybercriminals access your network, many other measures become useless. So double down on preventing unauthorized network access: implement network access control (NAC) solutions, use robust authentication methods, and ensure the physical security of your network devices.
- Use encryption. HTTPS, VPNs, and various encryption protocols protect traffic transmitted over the network. Attackers could still intercept traffic before it reaches the VPN because ARP spoofing occurs at the data link layer of the OSI model, below the layer where VPN encryption is applied. However, reliable encryption is an excellent measure to improve your network security nevertheless.