What is a backdoor attack? Definition, examples, and prevention
A backdoor attack is a type of cybersecurity threat that could put companies, websites, and internet users at risk. The term covers a wide range of common cyberattacks, targeting everyone from individuals to government agencies and international corporations. So what is a backdoor attack, and how dangerous can it be?
Contents
- What is a backdoor?
- How does a backdoor attack work?
- How dangerous is a backdoor attack?
- A brief history of backdoor attacks
- How do backdoors and trapdoors differ?
- Types of backdoor attack
- Is a backdoor attack classified as a trojan?
- Examples of backdoor attacks
- What are the laws regarding backdoor attacks?
- How to protect yourself from backdoor attacks
- What to do if you become a backdoor attack victim
- How to remove backdoors
What is a backdoor?
A backdoor is an undocumented way to bypass existing cybersecurity measures and gain access to the computer system or device. Software and hardware developers sometimes install backdoors into their own products to retain access for troubleshooting purposes.
Backdoor installation helps software developers solve various problems, for example, retrieve data from a device to aid a criminal investigation or restore users’ lost passwords. But the backdoors might also be exploited by hackers, but how?
How does a backdoor attack work?
Backdoor attacks work in two ways. Hackers might either discover and exploit a backdoor that already exists within a system, or they might install a backdoor into the system themselves.
In the first scenario, hackers use a backdoor to circumvent normal security measures and gain unauthorized access to a computer system and its data. In the second one, they exploit system vulnerabilities to gain access into it and implant backdoor software. Once the backdoor is in, attackers can easily re-enter the system whenever they like, even if the vulnerabilities are fixed.
Threat actors might use malware to set up an entry point into the system. When the malware infects the system, it brings in other harmful programs to make it possible to create a backdoor. For example, a rootkit infection can result in the creation of a backdoor in a system. Once the backdoor is set up, hackers send commands from a command-and-control server through this backdoor to steal data or damage the system.
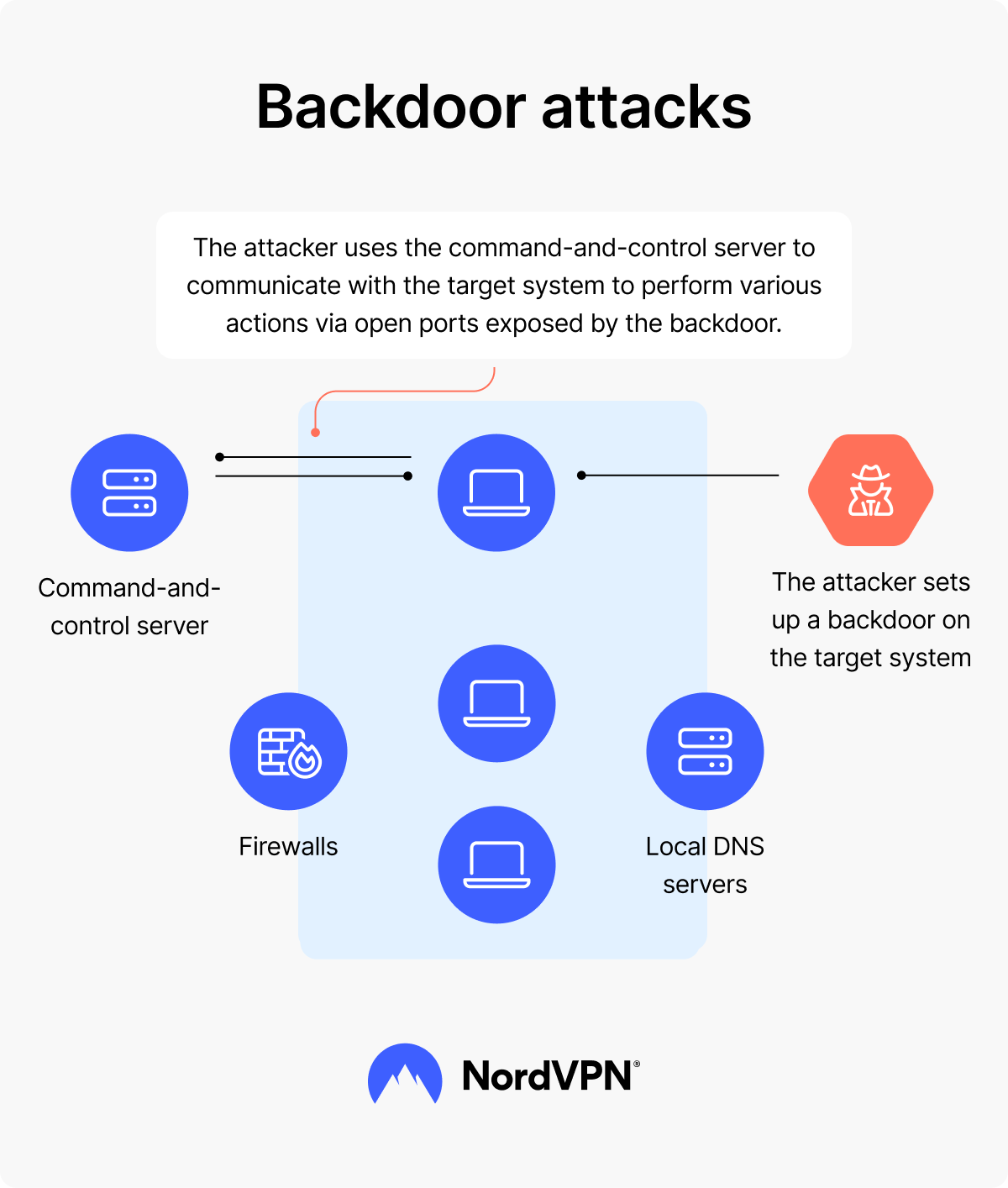
These attacks often go undetected, at least at first, because the hackers do not disrupt or brute force their way through any of the cybersecurity systems. Once they’ve got remote access to a network or device, they can install malware, engage in data theft, and spy on user activity.
How dangerous is a backdoor attack?
Backdoor attacks can be extremely dangerous because they often involve hackers gaining an extremely high level of access and privileges within a system or network. If they can do this without being detected, they can then squat there for months, monitoring user activity. Here are just some of the dangers posed by backdoor attacks.
- Massive data theft. If the backdoor attack has been successful, the hacker can ransack databases and steal private information.
- Spear phishing attacks. Hackers could use backdoors to access email accounts or other internal messaging systems within an organization and then send targeted phishing emails to the contacts of the compromised account. This may allow them to spread malware or backdoor trojans to other accounts.
- Cyber espionage. Backdoor attacks are the preferred strategy for cyber spies working on behalf of rival nation states. Unlike other forms of spying, these attacks don’t require physical access, so a successful backdoor hacker can spy on an enemy government from the other side of the world.
- Cyber warfare. While some hackers might just steal sensitive information, others could do a lot worse. Backdoor intrusions can allow state-backed hackers or even lone-wolf terrorists to carry out acts of cyber warfare. Power grids, water filtration plants, missile systems, and other important infrastructure essential for health and safety are all potentially vulnerable to backdoor attacks, and disruption in these areas could be catastrophic.
A brief history of backdoor attacks
A reference to backdoor attacks was first made in 1967, in a paper published at a conference of the American Federation of Information Processing Societies. The paper discussed the risks of “trapdoor” attacks. In 1984, Ken Thompson demonstrated the possibility of a backdoor attack by presenting how to modify a compiler to insert a backdoor in login authentication.
Flash forward to the 1990s, when backdoors started gaining notoriety for being a tool for unauthorized access by both hackers and government agencies. The US’s National Security Agency (NSA) began developing the Clipper chip project. In theory, this Clipper could be added to phones and computers, giving authorities a secure backdoor to all US devices. After an outcry from privacy and security experts, Clipper was abandoned.
Currently, the threat of backdoor attacks has expanded from standard internet-connected systems to the Internet of Things and cloud computing. But to this day, the NSA is accused of trying to insert or exploit backdoors in software and applications.
How do backdoors and trapdoors differ?
While some people use the phrase trapdoor and backdoor interchangeably in the cybersecurity context, the word trapdoor has another meaning in computing that is not related to this topic.
In cryptography, a “trapdoor function” is a process in which data can move in one direction easily but cannot be reversed without a special key or piece of information.
If someone is talking about a trapdoor attack, however, they are probably referring to backdoor attacks rather than referencing the cryptographic trapdoor function.
Types of backdoor attack
Backdoor attacks vary depending on the types of backdoors they use. We’ll explore those different options now.
Administrative backdoors
Lots of software developers include backdoors in their programs to give them easy administrative access to various areas of their own systems. Doing so can help them to troubleshoot user problems and fix vulnerabilities quickly. However, if these backdoors are discovered by cybercriminals, they can be used to launch cyberattacks.
Malicious backdoors
A malicious backdoor is one created for a malicious purpose. This process may involve hackers installing backdoor malware through a targeted phishing email. For example, a bad actor might infect the device of a government employee with a backdoor trojan, and then through the infected device they begin worming their way into whatever networks the employee has access to. If the hacker can eventually gain access to the code of an operating system, they can add backdoors to allow for easy access in the future.
Accidental backdoors
Many backdoors are just the result of human error. When a developer leaves a weak point in their internet security systems, it can go undetected for a long time. If bad actors find the flaw first, they can use it as a backdoor to the operating system or application.
Hardware backdoors
While most backdoor attacks involve hackers gaining remote access to networks and devices through software flaws, it’s also possible to include hardware backdoors in the physical structure of a device. A good example is the Clipper chip that the NSA proposed. However, this approach is high risk for a cybercriminal because it requires physical access to a targeted device.
Is a backdoor attack classified as a trojan?
A backdoor attack is not classified as a trojan. Trojans are pieces of malware that install themselves covertly, hiding inside another piece of software. If you download free programs or applications — especially those hosted on disreputable or high-risk sites — they may come bundled with trojans.
Backdoor attacks that rely on malware can often use trojan attacks as a delivery mechanism. However, the term “backdoor attack” is wide-ranging, so this is just one strategy.
Examples of backdoor attacks
There are numerous examples of backdoor attacks hitting companies and websites. Here are some of the most prominent backdoor attack cases:
- Cult of the Dead Cow. An early instance of a malicious backdoor appeared in 1998, when a hacking collective (Cult of the Dead Cow) created a form of malware to exploit weaknesses in the Windows operating system. This small program could be installed through a trojan without alerting the system’s user. It then allowed the hacker to remotely control the infected device.
- Juniper Networks. Ten years later, we find an example of an administrative backdoor. Juniper Networks (the same company that would later be the center of another backdoor-related controversy) deliberately built backdoors into the firmware on some of their products. With a preset master password, a user could gain administrative access to the system.
- SolarWinds. In 2020, the software company SolarWinds, which supplies software to US government agencies, was targeted by hackers. The attackers were able to install backdoors in SolarWinds software, allowing hackers to bypass security protocols and spy on the internal activity of the US government for almost a year.
What are the laws regarding backdoor attacks?
Backdoors can be perfectly legal, provided they are coded into software by the developers for legitimate reasons and used safely. As we’ve covered, backdoors can be a normal part of administrative and troubleshooting processes.
However, if a hacker finds or creates a backdoor and uses it to gain unauthorized access to a piece of software, they are breaking the law.
That doesn’t mean all hackers who go looking for backdoors are criminals, of course. Many white hat hackers work as penetration testers. These cybersecurity experts try to find accidental backdoors before the cybercriminals do so that the vulnerabilities can be patched.
How to protect yourself from backdoor attacks
Individuals can only do a limited amount to protect themselves from backdoor attacks because these incidents often involve large organizations and service providers rather than the devices of normal users.
However, if you’re an employee who’s worried about allowing hackers to sneak into your company, here are some steps you can take to protect yourself.
- Don’t use your work device for personal internet activity. Even if you don’t visit high-risk websites, it’s easy to accidentally click on a malicious ad or a phishing link, triggering a malware download. A work device, like a personal computer or phone, could be a hacker’s access point to the entire company, so it’s your responsibility to protect it. To do so, you can use anti-phishing software for an added layer of defense
- Report any unusual or suspicious incidents. If your device is acting strangely or you’ve received a suspicious email, report these potential red flags to superiors within your organization. If the company has a security team or specialist, contact them directly.
- Use a VPN, especially while traveling. Remote work is increasingly common, but connecting to public Wi-Fi in a local cafe, on a train, or in a hotel could be risky. These hotspots are often the hunting grounds of hackers, so use a VPN on your work device to keep your online activity private.
- Use strong passwords. Create strong and unique passwords for all your accounts, and change the passwords regularly. You can use a password manager to store your credentials so you don’t have to memorize them.
- Enable firewalls. Use both hardware and software firewalls to protect your network from unauthorized access.
- Monitor network traffic. Keep an eye on your network traffic for unusual activity, which might indicate a backdoor being used.
What to do if you become a backdoor attack victim
If you think you’re the victim of a backdoor attack, take these steps to limit the potential damage.
- Make a criminal complaint. If someone is accessing devices, files, or systems without authorization, that’s a crime, even if they’re taking advantage of a mistake you or someone in your organization made. Contact the authorities immediately.
- Inform coworkers and customers. The sooner everyone inside an organization — as well as consumers and clients — are made aware of the attack, the sooner they can take steps to protect themselves (limiting how much information they send over a compromised network, for example). It can be tempting to try to limit reputational damage by keeping the information to yourself, but in the long run this can escalate the situation.
- Start looking for trojans and malware. If a backdoor attack has taken place, it’s likely that malware and trojans may have been covertly installed on your operating systems. Look for any newly downloaded and unexplained programs and remove any of them that aren’t meant to be there. Some trojans are relatively harmless, but others could be facilitating a „backdoor“.
How to remove backdoors
While there are no silver bullets when it comes to completely removing malicious backdoors’, here are a few steps you can take.
- Run anti-malware programs. A good anti-malware program will be able to find and remove potentially malicious software running on your system. It’s best to have this software installed even if you’re not the victim of a backdoor attack, of course.
- Perform a full system reset if you think a specific device or operating system contains malware that is creating a backdoor. However, if the backdoor is coded into the operating system itself — for example, if the hackers are just taking advantage of a pre-existing administrative backdoor — a system rest won’t fix the problem.
- Manually remove malware. If the backdoor is the result of a piece of malware, you should be able to delete it manually. Some malware can be found easily or using the search function of some antivirus software. Once you’ve located the file in question, delete it and empty your trash bin.
Want to read more like this?
Get the latest news and tips from NordVPN.

