What is asymmetric cryptography?
Are your emails and messages encrypted? If they are, they most likely used asymmetric cryptography to shield your sensitive data from prying eyes. Find out more about this type of encryption, and its pros and cons compared to symmetric cryptography.

Contents
What is encryption?
To understand what asymmetric cryptography is, we first need to understand what encryption and encryption keys are.
Encryption is a process in which mathematical formulas called encryption algorithms are used to turn plain text into scrambled, unreadable ciphertext. To encrypt or decrypt the data, you also need a set of rules that would indicate the correlation between the original and encrypted texts. These are called encryption keys, which are just a string of numbers usually measured in bits.
Asymmetric cryptography explained
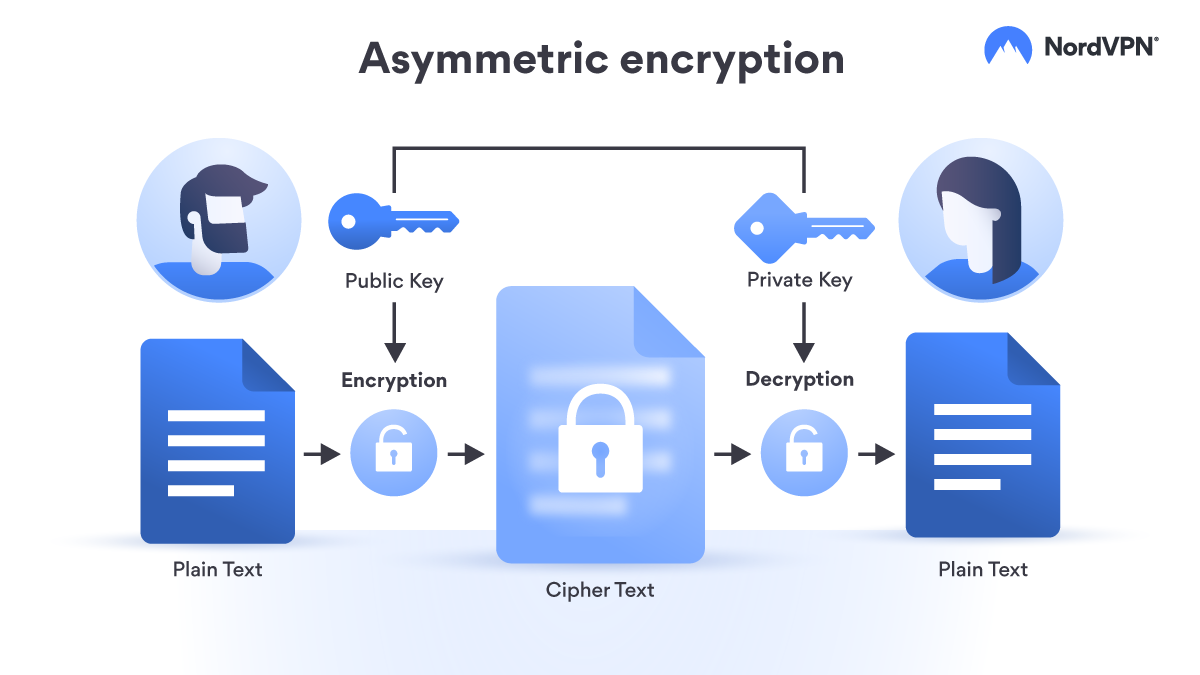
Asymmetric cryptography, otherwise known as public-key cryptography, is when two keys – private and public ones – are used to encrypt and decrypt data. Both keys are related in a way that you need one to encrypt information, and the other to decrypt it.
Usually, one key is made public so that anyone who wants to send you any data could use it for encryption, while the second key is kept private as you will use it for decryption. They ensure that one sender wouldn’t be able to read the messages sent by another sender, even though they both have the receiver’s public key. It’s also close to impossible to find out which private key belongs to which public key.
However, as public keys have to and are usually shared in public, this raises a concern — how do you know that the shared key hasn’t been tampered with or replaced by a hacker? There’s no perfect solution to this either. Some authorities issue certificates confirming the originality of the public key. This is mostly used to verify encrypted internet connections and digital signatures (for example, for HTTPS). On the other hand, there are encryption algorithms such as OpenPGP that rely on decentralized systems like a web of trust where individuals confirm the originality of the key.
How does asymmetric encryption work?
- The sender obtains the receiver’s public key (this can be from a public database or directly from the receiver).
- The sender uses the key to encrypt the message, data or file into ciphertext.
- The sender transmits the encrypted data over to the receiver.
- The receiver uses their private key to decrypt the message.
Asymmetric encryption algorithms
Popular asymmetric key encryption algorithms include EIGamal, Rivest–Shamir–Adleman (RSA), Digital Signature Algorithm (DSA), Elliptic curve cryptography (ECC), and PKCS. RSA is currently the most widely used algorithm. It’s found in the SSL/TLS protocols used to establish an encrypted connection between you and the websites you’re visiting. RSA keys are typically 1024, 2048 or 4096-bits long. Governments and the industry are now moving to a minimum key length of 2048-bits as they believe that the former types will soon be broken.
ECC is also getting more and more recognition from cybersecurity experts as it can create a faster, smaller, and more efficient cryptographic key. It’s also more challenging to break as it uses a more complex “problem” compared to RSA. Our new VPN protocol NordLynx uses ECC, as does our new file encryption app, NordLocker. You can read more about NordLocker and ECC here.
What is it used for?
- To encrypt your internet connection. Asymmetric cryptography is used in SSL/TLS handshakes, which help make your HTTPS connection secure.
- To encrypt messages and emails that use the OpenPGP or S/MIME protocols. Read more about encrypted messaging apps and encrypted emails in our blog posts.
- To digitally sign files and documents. With asymmetric cryptography, you can confirm whether the file was corrupted or edited in transit. Signing with a digital signature also means that the sender can’t deny sending a message as it links back to them.
- To complete cryptocurrency transactions. It ensures that only legitimate owners can spend their cryptocurrency.
- Asymmetric encryption is used in public key infrastructure (PKI) technology, which refers to secure online communications and safeguarding digital asset sharing on the public internet or company networks.
Symmetric vs. asymmetric cryptography
The main difference between the two is that symmetric encryption uses identical keys while asymmetric uses different but mathematically related keys. Symmetric encryption, which preceded asymmetric encryption, presented one big security issue — key distribution. How can you exchange keys over the internet if the connection isn’t secure? Anyone sniffing that traffic could grab your keys and then listen to any encrypted communication. The problem was solved by public key infrastructure, where the two parties don’t need to exchange session keys and one key always stays secret.
Asymmetric encryption isn’t flawless either. It takes more computing resources and time to encrypt and decrypt information. Its keys have to be longer to provide the same level of security that symmetric encryption does. For example, a symmetric key size of 80 bits would be equal to an RSA 1,024-bit key. This is why some protocols (like SSL/TLS) choose to use a mixture of the two — asymmetric encryption to establish a secure connection and exchange symmetric session keys, and then symmetric encryption for further communication.
Modern asymmetric encryption algorithms like ECC are designed to cut down the key length. For example, a 160-bit ECC key would be equivalent to an 80-bit symmetric key. However, it’s still not as fast as symmetric cryptography.
Want to read more like this?
Get the latest news and tips from NordVPN.