Ciphertext: All you need to know
Phones, digital television, websites, and ATMs all rely on ciphers to maintain security and privacy. But what is ciphertext? How does it differ from encryption? And where are ciphers used?
What is ciphertext
Ciphertext is encrypted plaintext. Plaintext becomes ciphertext when an algorithm called a cipher is used to make text or data unreadable.
What is the difference between plaintext and ciphertext?
Plaintext is turned into ciphertext through the process of encryption.
- Plaintext is text in normal readable language.
- Ciphertext is a series of randomized numbers and letters that humans cannot make sense of.
What is a ciphertext example?
The Caesar cipher is a substitution cipher where each letter in the plaintext is shifted down the alphabet. For instance, with a shift of 1, A would be B. With a shift of 2, A would be C. Polygraphic, permutation, transposition, and substitution ciphers are the most common ciphers used to turn plaintext into ciphertext (see types of ciphers below).
Here’s an example of the Caesar substitution cipher in action, with an alphabetical shift of 1.
Plaintext: London Bridge is burning
Ciphertext: Mpoepo Csjehf jt cvsojoh
Why is ciphertext used?
In cryptography, ciphertext is used to protect data and confidential information from being read by hackers or anyone else with bad intentions. The result is encrypted data.
Signal encrypts your messages so they can’t be read by Signal employees or adversaries. Your medical records are encrypted on hospital servers, and your online banking is secured with TLS encryption – that’s what the green padlock means next to the URL (see use cases below).
Encrypted data (ciphertext) can only be turned back into readable (plaintext) data with a decryption key.
Two types of keys exist in public-key encryption (or asymmetric encryption): a public key and a private key. A public key can only encode the data and a private key can only decode it.
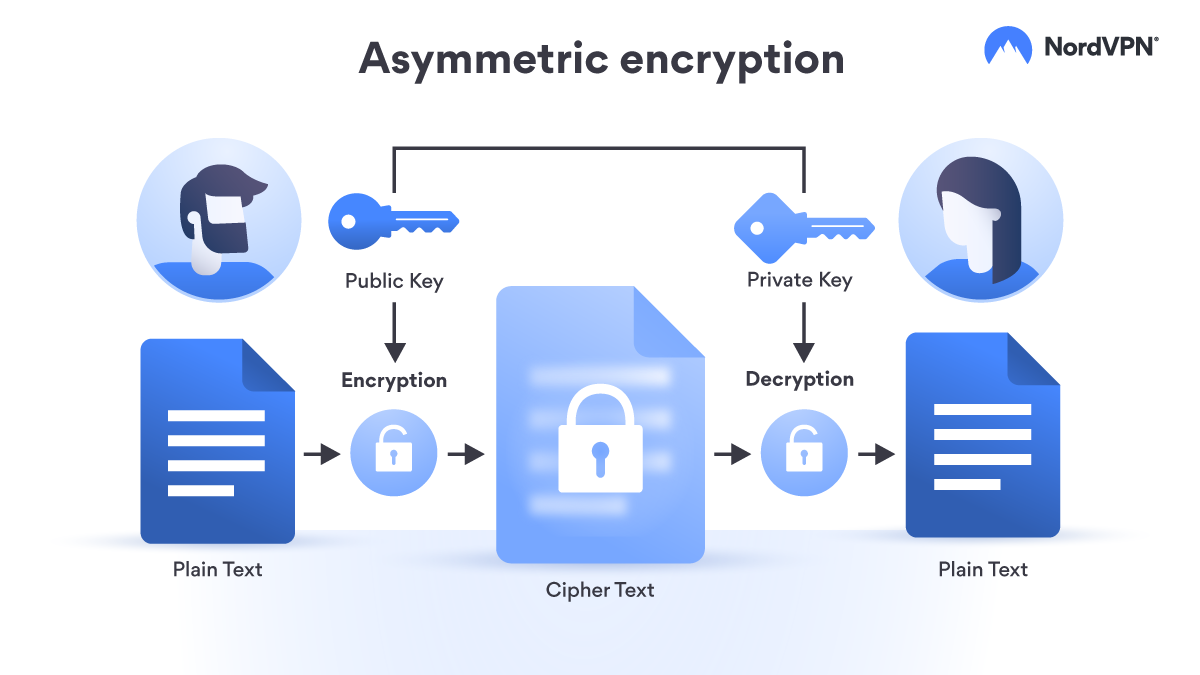
The difference between ciphertext and encryption
A cipher is an algorithm or process used to encrypt data, like AES, RSA, and DES. Encryption is the process of converting that data using a cipher.
Types of ciphers
Here we discuss the two main categories of ciphers and four other types of ciphers.
Block ciphers and stream ciphers
Ciphers fit into two categories: Block ciphers and stream ciphers.
- Block ciphers encrypt blocks of data that are a fixed size and measured in bits, like AES, DES, and 3DES.
- Stream ciphers encrypt continuous streams of data, like ChaCha, RC4, A5/1, A5/2, Chameleon, FISH, and Salsa20.
Example of a stream cipher
A stream cipher encrypts plaintext messages by applying an encryption algorithm with a pseudorandom cipher digit stream (keystream). Each bit of the message is encrypted piece by piece with the keystream digit.
Where are stream ciphers used?
Stream ciphers are used anywhere where speed and simplicity are needed. They’re often used in secure wireless connections like TLS, where plaintext is recieved in continuous unknowable lengths.
Example of a block cipher
A block cipher encrypts blocks of data with a symmetric key, as opposed to stream ciphers that encrypt bit by bit. AES encrypts bit blocks with predetermined key lengths like AES-128, 192, or 256 bits. Ciphers that use longer keys, measured in bits, take longer to crack and are more resistant to brute-force attacks.
Where are block ciphers used?
Block cipher encryption like AES encryption is one of the most secure encryption types as the recipient must possess keys to decrypt the message. Commonly used by governments and virtual private network companies, block cipher encryption is great for securing classified information either in storage or in transit on a network.
Polygraphic, permutation, transposition, and substitution ciphers
Polygraphic ciphers
Polygraphic ciphers work by dividing plaintext data into parts and replacing each group with a word, a single character, a number, a symbol, or any other group of characters.
A common technique is to assign several predefined words or numbers to popular words or phrases. Methods like these have been used in Europe for centuries. For example, diplomats used codenames to encode important institutions, places, and names of important people in communications.
Permutation ciphers
Permutation ciphers rearrange a linear set or number of things into a different order or sequence. For example, “Monday, Tuesday, Wednesday” could become, “Tuesday, Wednesday, Monday.”
Permutation ciphers are used when the order of the arrangements matters. They’re also often classified under transposition ciphers.
Transposition ciphers
Transposition ciphers take units of plaintext data and shift them according to a regular system. In the end, you get a permutation of the plaintext.
A simple example of a transposition cipher would be to reverse the order of the letters in the plaintext or to reverse the letters of each word, but not the order in which the words are written.
Substitution ciphers
Substitution ciphers replace characters in the original text with different letters, numbers, or other characters.
A simple example of a substitution cipher is where each letter of the alphabet is represented by a number, like 1 for A and 2 for B.
Ciphertext attacks
Attacking a cipher is an ambitious move because hackers will often try to recover the key in use rather than simply expose the plaintext of a single ciphertext. AES cipher encryption, for example, has never been cracked, but that doesn’t mean hackers won’t try.
There are two approaches to attacking a cipher: cryptanalysis and brute-force attack.
Cryptanalysis
Cryptanalysis is the method used to try to read the contents of encrypted messages. Cryptanalysts will look for weaknesses in systems to breach cryptographic security systems and reveal the contents of encrypted messages even if the cryptographic key is unknown.
Brute-force attack
In a brute-force attack, millions of combinations per minute are tried in attempts to crack a code. Ciphers that use longer keys, like AES-192 or AES-256-bit key length, are more effective against brute-force attacks because the longer the key length, the more attempts are needed to expose the plaintext.
That’s part of the reason why NordVPN uses AES-256-bit encryption to secure the traffic of millions of customers worldwide. A key length of 256 means that our encryption has 2,256 possible key combinations (a number 78 digits long) and would take billions of years to crack with today’s computers.
Want to read more like this?
Get the latest news and tips from NordVPN.